A banking Trojan striking corporate targets across Brazil has been unmasked by researchers.
On Tuesday, ESET published an advisory on the malware, which has been in development since 2018.
Dubbed Janeleiro, the Trojan appears to be focused on Brazil as a hunting ground and has been used in cyberattacks against corporate players in sectors including healthcare, engineering, retail, finance, and manufacturing. Operators have also attempted to use the malware when infiltrating government systems.
According to the researchers, the Trojan is similar to others currently operating across the country — such as Casbaneiro, Grandoreiro, and Mekotio — but is the first detected that is written in .NET, rather than Delphi, which is usually favored.
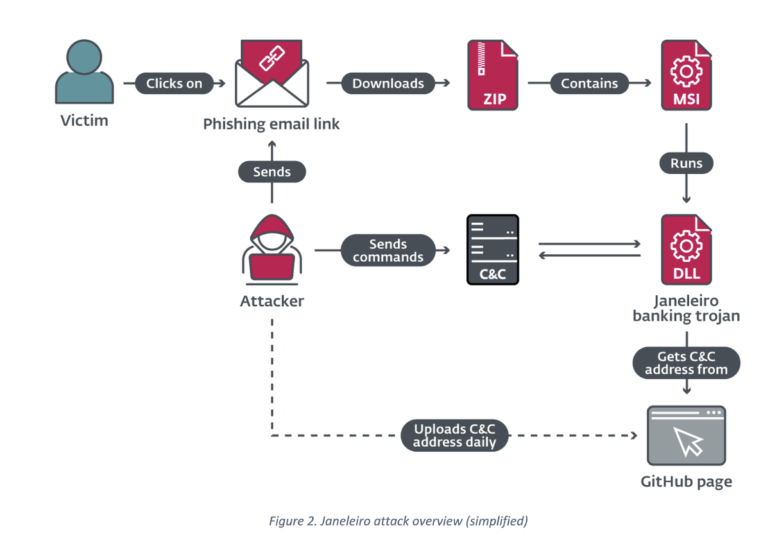
Phishing emails, sent in small batches, are sent to corporate targets pretending to relate to unpaid invoices. These messages contain links to compromised servers and to the download of a .zip archive hosted in the cloud. If the victim unzips this archive file, a Windows-based MSI installer then loads the main Trojan DLL.
“In some cases, these URLs have distributed both Janeleiro and other Delphi bankers at different times,” ESET says. “This suggests that either the various criminal groups share the same provider for sending spam emails and for hosting their malware, or that they are the same group. We have not yet determined which hypothesis is correct.”
The Trojan will first check the geolocation of the target system’s IP address. If the country code is other than Brazil, the malware will exit. However, if the check is passed, the malware will then collect a variety of operating system data and will grab the address of its command-and-control (C2) server from a dedicated GitHub page.
Janeleiro is used to create fake pop-up windows “on-demand,” such as when banking-related keywords are detected on a compromised machine. These pop-ups are designed to appear to be from some of the largest banks across Brazil and they request the input of sensitive and banking details from victims.
The malware’s command list includes options for controlling windows, killing existing browser sessions — such as those launched in Google Chrome — capturing screens, keylogging, and hijacking clipboard data, among other functions.
The operator of the Trojan appears to prefer a hands-on approach and may control the windows remotely, in real-time.
Most malware operators at least make a token attempt to conceal their activities. In this case, code obfuscation is light but there is no attempt to circumvent existing security software and no custom encryption.
The operator uses GitHub, a code repository, to host files containing C2 server lists to manage Trojan infections. These repositories are updated on a daily basis.
As of March, four variants of Janeleiro have been detected in the wild, although two share the same internal version number. Some samples have been packaged together with a password stealer in attacks, which suggests “the group behind Janeleiro has other tools in their arsenal,” according to the team.
ESET says that GitHub has been made aware of the threat actor’s account and abuse of the platform. The page has now been disabled and the owner suspended.
“GitHub values the contributions of our security research community and is committed to investigating reported security issues,” a GitHub spokesperson told ZDNet. “We disabled the page in accordance with our Acceptable Use Policies, following the report that it was using our platform maliciously.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0