by Sara Rebein, Leibniz-Institut für Analytische Wissenschaften – ISAS – e. V. Artificial intelligence (AI) has become an indispensable component...
The key to understanding proteins—such as those that govern cancer, COVID-19, and other diseases—is quite simple: Identify their chemical structure...
An operating system’s kernel acts as the translator between user and machine. To improve the reliability of a kernel, developers...
Security pros say it’s one of the worst computer vulnerabilities they’ve ever seen. They say state-backed Chinese and Iranian hackers...
The Solarwinds software supply chain attack is the one everyone knows about. But supply chain attacks are becoming commonplace, and...
Microsoft Microsoft is getting ready to make Windows 10 21H2 available to mainstream users. In an October 21 blog post,...
Tech leaders have been vocal proponents of the need to regulate artificial intelligence, but they’re also lobbying hard to make...
A research team at Illinois Institute of Technology has extracted personal information, specifically protected characteristics like age and gender, from...
Researchers have pioneered a technique that can dramatically accelerate certain types of computer programs automatically, while ensuring program results remain...
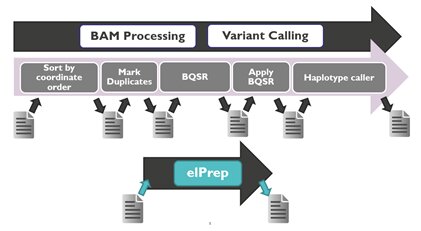
The cost of sequencing has gone down tremendously. But still it is not used in daily practice. One of the...
UK supermarket giant Tesco has restored access to its website and app after an outage struck the service on Saturday,...
Apple For the past few years, I’ve been wondering how the Intel era was going to end. At Apple’s Unleashed...