A research team led by faculty from Binghamton University, State University of New York has been exploring how mass layoffs...
Chatbots powered by artificial intelligence (AI) can pass a cybersecurity exam, but don’t rely on them for complete protection. That’s...
A team of researchers at the University of Texas at Arlington has developed software that prevents artificial intelligence (AI) chatbots...
As travelers rush to book their summer getaways, Booking.com’s internet safety boss says watch out for supercharged AI scams. Marnie...
Speak a little too haltingly and with long pauses, and OpenAI’s speech-to-text transcriber might put harmful, violent words in your...
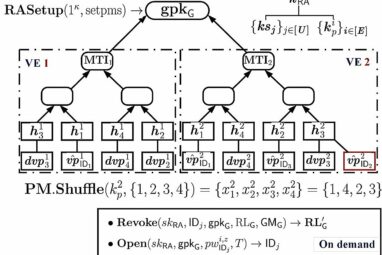
“Please enter the code within the next two minutes.” The concept of one-time passwords (OTPs) has become a mainstay in...
Researchers have collected and analyzed an unprecedented amount of data on SMS phishing attacks, shedding light on both the scope...
Leading AI scientists are calling for stronger action on AI risks from world leaders, warning that progress has been insufficient...
It’s one thing to dream up a quantum internet that could send hacker-proof information around the world via photons superimposed...
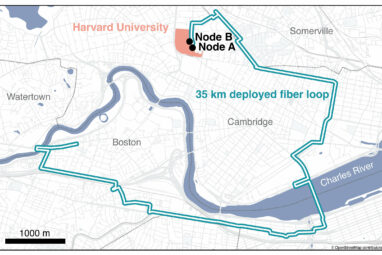
Advanced information processing technologies offer greener telecommunications and strong data security for millions, a study led by University of Maryland...
Advanced information processing technologies offer greener telecommunications and strong data security for millions, a study led by University of Maryland...
The news about the Israel-Hamas war is filled with reports of Israeli families huddling in fear from relentless rocket attacks,...