In a joint security alert published on Thursday, the US Cybersecurity Infrastructure and Security Agency, along with the Federal Bureau of Investigation, warned about increased cyber-attacks targeting the US K-12 educational sector, often leading to ransomware attacks, the theft of data, and the disruption of distance learning services.
“As of December 2020, the FBI, CISA, and MS-ISAC continue to receive reports from K-12 educational institutions about the disruption of distance learning efforts by cyber actors,” the alert reads.
“Cyber actors likely view schools as targets of opportunity, and these types of attacks are expected to continue through the 2020/2021 academic year,” it added.
Ransomware attacks
But of all the attacks plaguing the K-12 sector (kindergarten through twelfth-grade schools), ransomware has been a particularly aggressive threat this year, CISA and the FBI said.
“According to MS-ISAC data, the percentage of reported ransomware incidents against K-12 schools increased at the beginning of the 2020 school year,” the two agencies said.
“In August and September, 57% of ransomware incidents reported to the MS-ISAC involved K-12 schools, compared to 28% of all reported ransomware incidents from January through July,” they said.
The numbers are also consistent with a recent Emsisoft report where the company also noted a surge in ransomware attacks against the educational sector in Q3 2020.
The five most active ransomware groups targeting the US K-12 this year have been Ryuk, Maze, Nefilim, AKO, and Sodinokibi/REvil, according to reports received by the two agencies.
Making matters worse, all five are ransomware operations known to run “leak sites” where they usually dump data from victims who don’t pay, which also creates the danger of having student data published online.
Commodity malware
But an increase in ransomware attacks wasn’t the only problem that K-12 schools faced this school year. CISA and the FBI said that mundane commodity malware has also made its way on the networks of US K-12 organizations.
“These malware variants are purely opportunistic as they not only affect educational institutions but other organizations as well,” the agencies said.
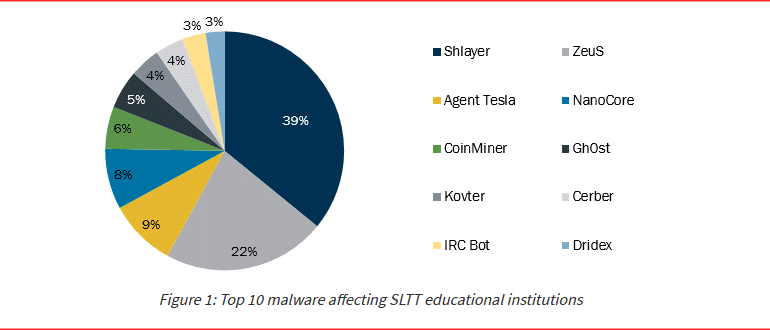
Among the most common malware infections seen on K-12 networks, the ZeuS (or Zloader) trojan (Windows) and Shlayer loader (macOS) have topped the infection charts.
The presence of this malware shouldn’t be taken lightly, as these threats can often turn into bigger intrusions at the drop of a hat and, normally, need to be addressed right away.
DDoS attacks and video conference disruptions
But on top of malware, which can lead to IT staff shutting down networks to deal with infections, the two agencies also warned K-12 schools to take care to protect themselves against other forms of cyber-attacks that can also cause disruptions, albeit more temporary.
These included distributed denial of service (DDoS) attacks and live video conference disruptions (also known as Zoom bombing).
With school IT systems now needing to work at full capacity in order to keep school resources up and running, DDoS attacks have been recently a favorite attack vector used to either ransom schools for a monetary profit or by the students themselves in order to get out of online classes.
Both Check Point and Kaspersky have already noted earlier this year that DDoS attacks against the educational sector have increased not only in the US but worldwide, as schools have moved their operations online.
As for video conference disruptions, this has been an issue for schools since March 2020 and has never gone away.
“These disruptions have included verbally harassing students and teachers, displaying pornography and/or violent images, and doxing meeting attendees,” CISA and the FBI said.
The alert published by the two agencies includes a long list of countermeasures that K-12 schools —and everyone else— can apply to prevent the most common threats they’ve seen this year.
“A combination of basic cyber hygiene, such as patch management, verifying compliance with strong password management policies, performing regular backups of essential systems that are not accessible from the same network, and ensuring that systems are protected with security software at the endpoint and gateway can help address some of these threats,” Satnam Narang, staff research engineer at Tenable, told ZDNet.
“Social engineering is still a viable tool in the cybercriminal’s toolkit, so regularly performing security awareness training is another weapon in the fight against these attacks.”