Security researchers have discovered a new malware strain with spying and surveillance capabilities —also known as spyware— that is currently available in both Android and iOS versions.
Named Goontact, this malware has the ability to collect from infected victims data such as phone identifiers, contacts, SMS messages, photos, and location information.
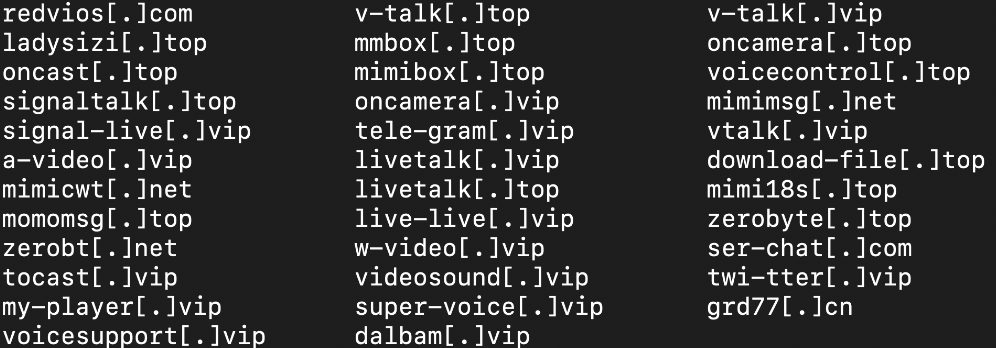
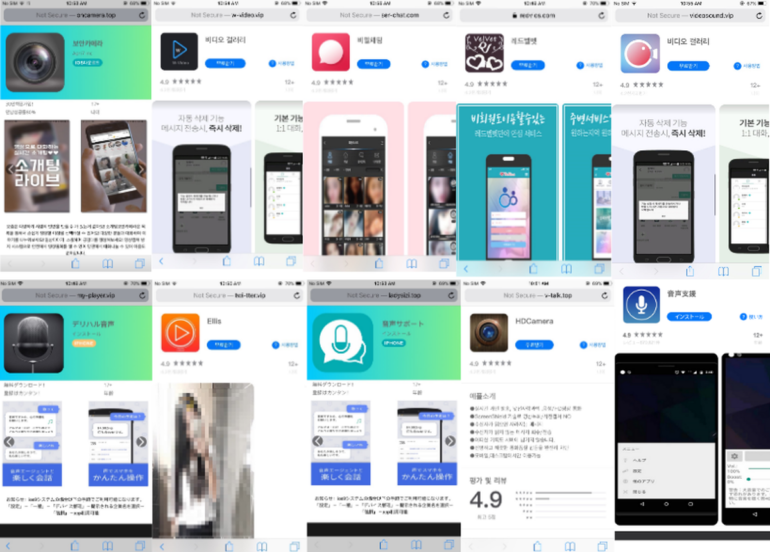
Detected by mobile security firm Lookout, the Goontact malware is currently distributed via third-party sites promoting free instant messaging apps dedicated to reaching escort services.
The target audience of these sites appears to be limited at the moment to Chinese speaking countries, Korea, and Japan, Lookout said in a report shared today with ZDNet.
Although the malware has yet to reach official Apple and Google app stores, there are signs that users are downloading and side-loading Goontact-infected applications.
Data collected from these apps is sent back to online servers under the Goontact operators’ control. Based on the language used for the admin panels of these servers, Lookout believes the Goontact operation is most likely managed by Chinese-speaking threat actors.
Links suggest connection to past sextortion campaign
Apurva Kumar, Staff Security Intelligence Engineer at Lookout, told ZDNet that the Goontact operation is very similar to sextortion campaign described by Trend Micro in 2018 (PDF).
Although there is no tangible evidence at the moment, Kumar believes that data collected through these apps could later be used to extort victims into paying small ransoms or have their attempts to arrange sexual encounters exposed to friends and contacts.
“We have notified both Google and Apple of this threat and are actively collaborating with them to protect all Android and iOS users from Goontact,” Kumar told ZDNet in an email over the weekend.
“Apple has revoked the enterprise certificates used to sign the apps and, as a result, the apps will stop working on devices,” the Lookout security engineer added.
“Play Protect will notify a user if any Goontact Android samples are installed on their device.”
The names of all Goontact-infected apps is pretty exhaustive and is too long to list here, but can be found at the end of this Lookout report, in case users want to check and see if they’ve downloaded and installed any of the apps. The sites that usually peddled Goontact-infected apps are listed below.