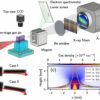
A Spanish student released a free decryption utility that can help victims of the Avaddon ransomware recover their files for free.
Published on GitHub by Javier Yuste, a student at the Rey Juan Carlos University in Madrid, the AvaddonDecrypter works only in cases where victims have not powered off their computers.
The tool works by dumping an infected system’s RAM and scouring the memory content for data that could be used to recover the ransomware’s original encryption key.
If enough information is recovered, the tool can then be used to decrypt files and help victims recover from Avaddon attacks without needing to pay the gang’s ransom demand.
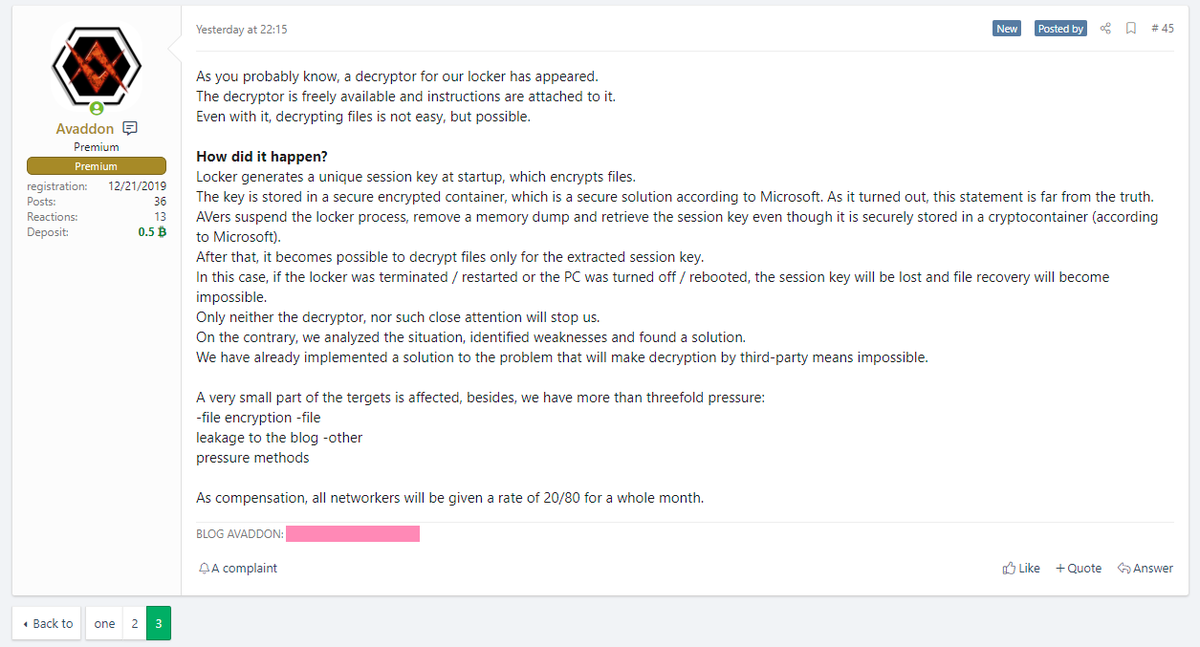
Avaddon gang fixes their code
But while the tool’s release will most likely help past victims, it won’t be helping companies that fall victim to new Avaddon attacks.
This is because the tool’s release did not go unnoticed. In a forum post on Wednesday, the Avaddon gang said it also learned of Yuste’s decrypter and has already deployed updates to its code, effectively negating the tool’s capabilities.

The Avaddon team’s reaction mirrors how the Darkside ransomware crew also answered the release of a similar decrypter for their own strain last month, in January.
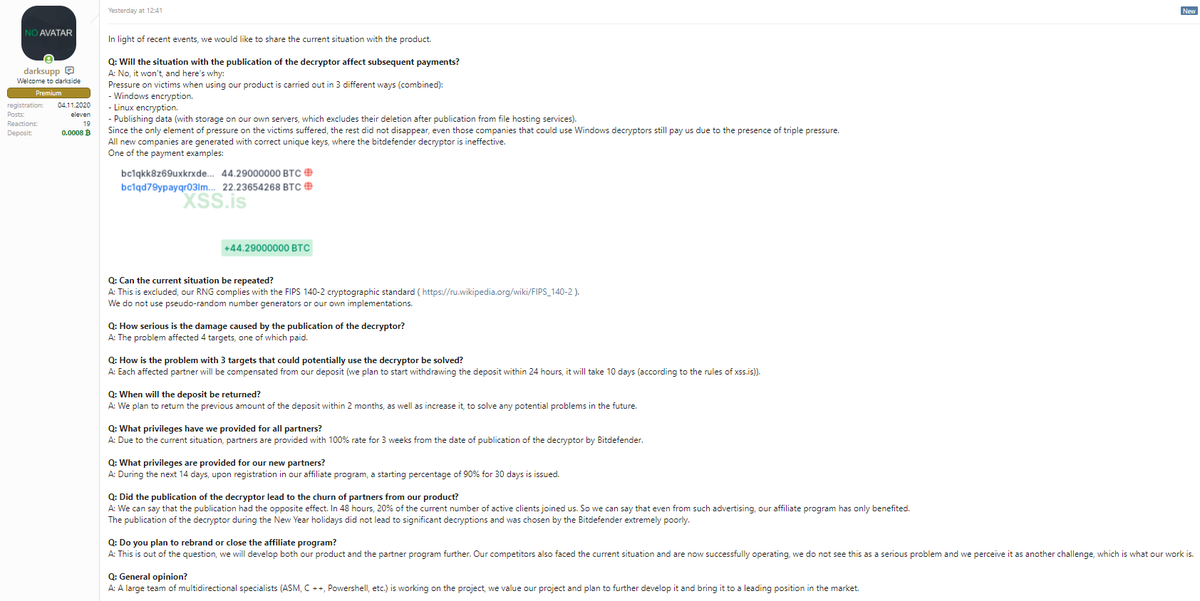

Infosec experts: Keep some ransomware decrypters private!
In the end, the release of both decryption utilities had a very limited impact. While a few victims were able to decrypt files, once the existence of the decryption tool was made public, the ransomware gangs analyzed how the tools worked and fixed their code within days.
The release of these two tools, along with a blog post from Dutch security firm Eye Control showing how victims could recover from attacks with the Data Doctor ransomware, has rekindled, once again, a years-long conversation in the cyber-security industry about how decryption utilities should be handled and released to victims.
Several prominent security researchers with a long history of helping ransomware victims since the mid-2010s have made their opinions known again over these past two months, highlighting the fact that decryption utilities that take advantage of ransomware encryption bugs should be kept private and distributed to victims via non-public channels rather than advertised online.
Furthermore, even if such tools need to be made public, there should not be any technical details that accompany the tool’s release, details that will obviously help the attackers patch their own code as well.
Good work, but it is nothing sensational… Actually, it would be much more helpful (or maybe even say, only would be helpful) if he not published this only says something like “if you got Avaddon ransomware, contact me immediately”.
😫
cc @demonslay335— MalwareHunterTeam (@malwrhunterteam) February 9, 2021
Keep it in you pocket folks! You can help victims and hold that blog post till AFTER the TA patches..
win win!— Bill Siegel (@billseagull) January 9, 2021
You could have just posted that you have a fix for this particular ransomware and ask people to reach out to you. Then reach out to initiatives like NoMoreRansom or communities like BleepingComputer to propagate the news. You know, like everyone else who is responsible.
— Fabian Wosar (@fwosar) January 9, 2021
On the other side, decryption utilities that are built around master decryption keys obtained from the attackers’ servers are OK to share online, as there’s little that ransomware authors can do about these tools.
All in all, seeing how the Avaddon and Darkside groups have reacted —by fixing their encryption schemes within days— it’s hard to argue against the arguments made online over the past two months, namely that some decryption tools should never make it into the public domain.