The expulsion of Huawei-made equipment from countries’ 4G and 5G Wireless networks resumes in earnest, with projects such as BT’s $701 million effort to rip and replace it all with Nokia and Ericsson equipment by 2027. The reason originally cited was the danger of a security threat, where China’s government could one day exploit Huawei equipment’s already documented vulnerabilities to clandestinely gather data, for example, on its own citizens abroad.
That couldn’t happen, say scientists and engineers in the emerging field of quantum key distribution, if the world’s telcos were to install QKD equipment in 5G Wireless base stations. These facilities are linked to one another by fiber optic cable. This same cable, the engineers say, could be leveraged to provide impenetrable communications, from which neither China nor anyone else could glean information.
“Although we think of 5G and 4G and cellular and wireless technology, underpinning all of that is a very large fiber optic network. And that fiber optic network needs securing,” remarked Dr. Duncan Earl, currently president and CTO of California-based QKD firm Qubitekk Inc., and an 18-year veteran scientist at Oak Ridge National Laboratories.
Dr. Earl told the Inside Quantum Technology New York virtual conference on Wednesday that existing technology — not tomorrow’s quantum discoveries — could provide a long-term security solution for all 5G equipment, including but not limited to Huawei’s. He characterized this solution as “obvious.”
“There’s a big concern over foreign equipment being located or used on a 5G network,” stated Earl, using very diplomatic language. “In these base stations. . . you may be installing equipment that actually is tapping into those communications.” But that “foreign equipment” may have a cost advantage over alternatives from other manufacturers, he went on, especially in building out 5G networks in rural areas. (Huawei’s and ZTE’s price advantages are so well-documented, that this topic alone has become a discussion point in national security circles.)
“You could use quantum technology to essentially hop over these base stations,” Earl said.
Leap frog
Fronthaul fiber is what the telecom industry calls the fiber optic connections leading from antennas to baseband units (BBU) located in telco central offices. On the other end, backhaul connections lead from central offices to the transmitters throughout the wireless network — which happen to share tower space with antennas. In fact, the overlapping connections themselves have come to be known as crosshaul.
At the antenna end, a QKD transceiver could encrypt all fronthaul data flowing into the BBU, Earl suggested. That encryption would be bonded by physics rather than cryptography — an encryption so strong that the very act of intrusion would break the connection (which may instantly be re-established using a new quantum key).
“So the base station only would see encrypted payloads,” he said. “Once those were sorted and routed, as they left the base station, they would be decrypted by another quantum system.” This would allow the Radio Access Network (RAN) to continue to operate exactly as it does now, without retrofitting or re-engineering.
Last year, Earl’s Qubitekk purchased the complete QKD patent portfolio of Hampshire, UK-based defense contractor QinetiQ Ltd.
In a cellular network, data may traverse a variety of base stations. But one of the curious, even bewildering, phenomena of quantum networks is that the entanglement between qubits at the source and the eventual destination, establishes a kind of ethereal link between them, even in the absence of a direct fiber connection. Thus any quantum bond from point to point would be just as secure as if the network solely had those two points.
This phenomenon, says Dr. Earl, referring to recent experiments that provide incontrovertible evidence to his point, means that encryption effectively “hops over the base stations.”
Testing this principle in a real-world scenario today is the UK’s largest telco, BT. Last November, at the height of the pandemic, BT announced it would be leading a handful of startup quantum firms in building demonstrations of a key distribution system called AIRQKD, with backing from the UK Government’s Industrial Strategy Challenge Fund (ISCF).
“I could’ve done it from home”
Explaining the demonstration was BT’s senior manager of optical networks research and 36-year veteran of the company, Prof. Andrew Lord of the University of Bristol. In one real-world demonstration, QKD linked two buildings, one whose data center hosted architectural designs of the sort a firm would want to keep secret, and the second sporting a 3D printer. The intellectual property of such designs, remarked Prof. Lord, would be of the variety whose encryption would need to last 20 years or longer — well past the date when engineers believe current Public Key Infrastructure (PKI) would have been rendered pointless by quantum encryption. Those two buildings were linked by way of nearby base stations, whose quantum keys were secured over BT’s existing fiber infrastructure.
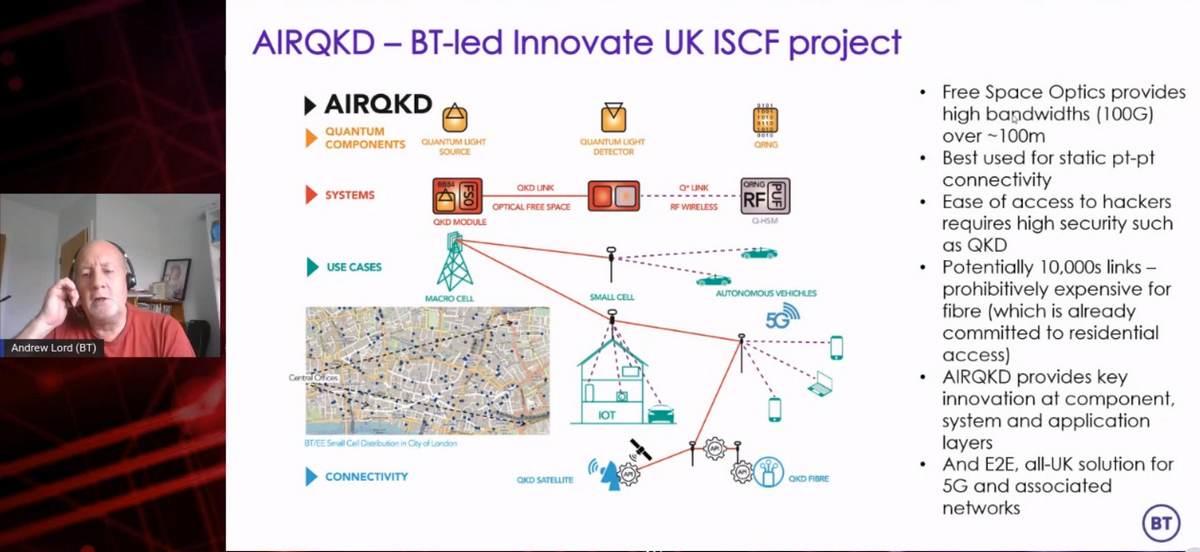

As the above diagram depicts, QKD transceivers would be installed at BT’s existing large 5G base stations, shown above as macro cells. Each macro cell would backhaul encrypted data to the smaller exchange cells, many of which are installed atop buildings. Theoretically, said Lord, the same encryption principle could be deployed for the 5G network’s control plane, safeguarding it from any malicious influence. When the system comes to full fruition, it could distribute quantum encryption keys literally over the air — perhaps via low-Earth orbit (LEO) satellite, or over line-of-sight distances (“free space”) as short as 150 meters.
For deploying such a system on existing 5G networks, “I can’t see any intrinsic problem,” reported Prof. Lord. “The backhaul distances would be 20 km, maybe a bit more. QKD is more than capable of doing that. So I don’t see a physical limit. In terms of data throughput, again, not a problem, because you transmit a key, and you use that key to protect a lot of data — [perhaps] a terabit of data. Then you need to refresh the key. QKD key rates are obviously quite low, but they’re certainly plenty enough to protect 5G backhaul links.”
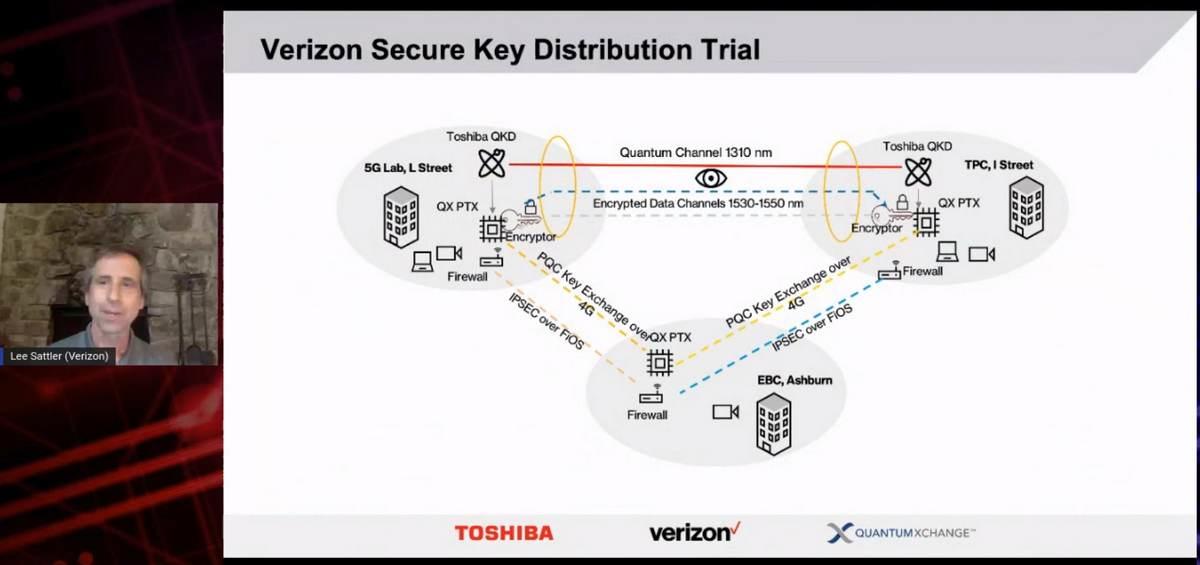

For America’s part, Verizon Distinguished Engineer Lee Sattler presented news of his company’s similar trials with line-of-sight QKD in the Washington, DC area, conducted in partnership with key distribution system provider Quantum Xchange. The diagram above shows the setup: a communication between the company’s 5G technology labs, and down the street about 4.5 km at its its Technology Policy Center. The two locations are linked by Verizon-owned dark fiber.
Using wave division multiplexing, Sattler told the IQT audience, his team created one optical channel at 1310 nm, and two encrypted data channels at 1330 and 1350 nm. Key management points in this diagram are called Phio Trusted Exchange points, named for Quantum Xchange’s Phio system. Its key selling point is the ability to exchange encryption keys out-of-band — that is, outside the network being encrypted, enabling any number of possible key exchange media, perhaps simultaneously. Those keys, in this case, are capable of securing Layer 2 communication, at the deep end of the network.
“We have an encryptor which can make requests to the PTX, to get the keys for a symmetric encryption session between the two locations,” explained Sattler. “When one encryptor at the 5G Lab site requests a key from its PTX, the PTXes have a conversation, agree upon a key pair, and provide that to the two encryptors at both ends. Then we have a nice, safe, secure data exchange between the two locations.”
By adding the Ashburn, Virginia location, and securing all PTX points with firewalls, a separate PTX network comes into existence — performing one of the key functions of a quantum network, without a quantum network. In this case, using PQC methods, all the PTX points can exchange keys over a 4G link — not even 5G. Alternately, the team could have used Verizon’s FiOS network. The PTX system is designed to enable other key distributions as well, most notably QKD.
“This concept is so simple,” said Sattler, “I could’ve done the same thing at my home. The PTX is a small form factor. I could easily have a PTX at my house and a firewall at my house, connect into this network, and have it be secured over IPsec, if I so desire.”
Who’s building the wall now?
In both 4G and 5G, the radio access network (RAN) is separated from the network control plane of SDN, confining it to the user plane. An analysts’ report produced in 2019 by Ovum and distributed by Ericsson entitled “The Facts on 5G” [PDF] made the case that this confinement is for the protection of user data, which can then be encrypted (using classical technology), passing through the core network without exposure.
Famously, in the act of publishing this paper, Ericsson declared, “Technically however, this is wrong.” The 5G base station, wrote Ericsson security engineers Patrik Teppo and Karl Norrman, “is the termination point for encryption and integrity protection and, potentially, the user plane can be accessed in clear text (in case over the top end-to-end encryption is not used). Therefore, the user plane traffic is, in this case, accessible to anyone controlling the [base station] or its implementation.”
Norrman and Teppo made the case that securing the RAN, therefore, is just as important a goal as securing the core. In so doing, they implied that chaining base stations together with what quantum engineers call “classical encryption” creates any number of weak points in the network — weak points that 3GPP, the industry consortium that formalizes 5G standards, may have left unaddressed.
Dr. Earl’s explanation and Prof. Lord’s demonstrations may shine a bright, photon-filled light on a permanent solution to this situation. At least theoretically for now, the types of security vulnerabilities cited by the UK’s National Cyber Security Centre could actually become impossible.
Standing in the way of such an outcome, however, in easily the utmost of ironies, may be the US National Security Agency. Beginning in 2015, the NSA took the stance that quantum encryption was a threat to national security, and tasked the National Institute of Standards and Technology (NIST) with choosing “post-quantum” cryptography methods (PQC) that could replace current-day PKI. In 2019, the NSA’s research director suggested the very search for PQC solutions, if made too public and shared with too many folks, could itself be a threat to security.
In April, NIST published guidance on its PQC efforts to date [PDF]. In it, the agency characterized the still-forthcoming date when a quantum algorithm (specifically, Shor’s Algorithm) breaks PKI as “a particularly disruptive cryptographic transition.” That transition, the report goes on, can only be met by rapid and fundamental improvements to classical cryptography methods. The report does not even mention the existence of QKD.


“Today, the NSA has a very blunt perspective,” remarked Qubitekk Vice President of Engineering K. Karunaratne, speaking at the IQT conference. “Really, the intent we want is, persuade them — and I agree that’s a very hard task — that QKD does have a place, for its specific use cases.”
Why does the NSA take such an antagonistic position, asked IQT Research’s Lawrence Gasman. “I think a fair amount of their attitude,” responded Karunaratne, “is based on a lack of knowledge of what QKD really is, and how QKD has been implemented.”
In his communications with government officials, including with NIST, Karunaratne said, some believe their policy toward “responding” to QKD has already been finalized. “A lot of these challenges, I think, are dated,” he went on, “and they’re based in a lack of knowledge on the NSA’s part, about what modern QKD is, and how it’s implemented.”
China may actually be working toward the same goal — not so much a quantum internet with interlinked QKDs, that’s the dream of engineers worldwide. Rather, a PQC initiative that ostentatiously, perhaps with photographic evidence, demonstrates China’s willingness to build its own quantum wall.
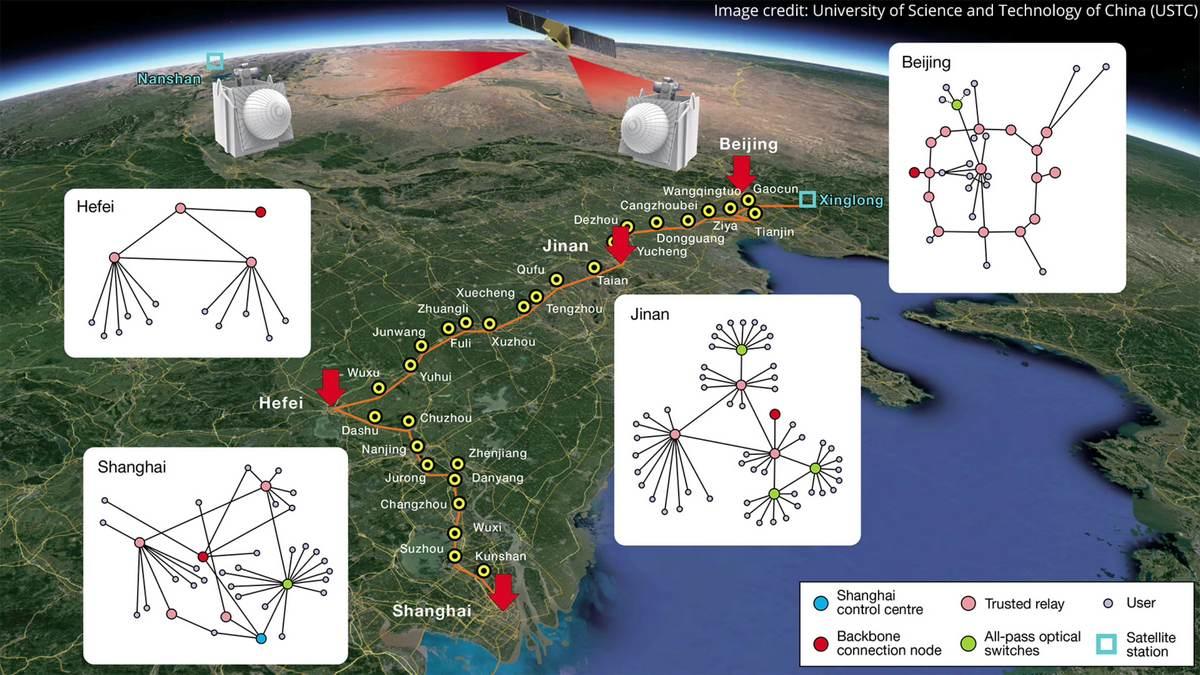

In January, students from the University of Science and Technology of China (USTC) reported in the journal Nature that they had already built a fiber optic network spanning 4,600 kilometers, incorporating more than 700 QKD links, including two satellite-to-ground transceivers. Those transceivers are apparently capable of generating entangled photon pairs, and transmitting them to any point in the network — space providing the shortest, least disruptive path between two points.
“The entire network is not completely quantum secure,” reported Tom Stefanick, visiting fellow at the Brookings Institution, “in the sense that they [USTC] have some 32 intermediate stops that are what they call ‘trusted nodes.’ They’re not quantum secure, but they’re secure enough that they’re considered intermediate routes for passing on the information.”
In a way, the USTC network may suffer from the same class of problem that Ericsson pointed out in encrypted 4G/5G: every stopover point may introduce a point of weakness. Theoretically at least, QKD promises a permanent solution to this problem, if that curious phenomenon can be successfully exploited. Perhaps China’s researchers would care for some help.
“There’s kind of a theme in the China/US confrontation,” remarked Stefanick. “China has a history of doing anti-satellite tests, and has an anti-satellite program. But as the same time, as they develop quantum and global communications, they’re going to need space. They’re going to start approaching the United States, in terms of their need and reliance on a stable regime in space. There aren’t lots of opportunities; that’s an opportunity to have discussions about stabilizing the domain of potential conflict.”