In the cyber-security field, the term OST refers to software apps, libraries, and exploits that possess offensive hacking capabilities and have been released as either free downloads or under an open source license.
OST projects are usually released to provide a proof-of-concept exploit for a new vulnerability, to demonstrate a new (or old) hacking technique, or as penetration testing utilities shared with the community.
Today, OST is one of the most (if not the most) controversial topics in the information security (infosec) community.
One one side, you have the people who are in favor of releasing such tools, arguing that they can help defenders learn and prepare systems and networks for future attacks.
On the opposing side, you have the ones who say that OST projects help attackers reduce the costs of developing their own tools and hiding activities into a cloud of tests and legitimate pen-tests.
An interactive map for OST usage
These discussions have been taking place for more than a decade. However, they have always been based on personal experiences and convictions, and never on actual raw data.
This is what Paul Litvak, a security researcher for cyber-security firm Intezer Labs, has tried to address earlier this month, in a talk at the Virus Bulletin security conference.
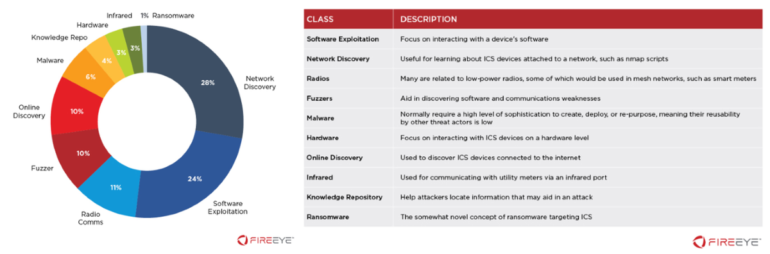
Litvak compiled data on 129 open source offensive hacking tools and searched through malware samples and cyber-security reports to discover how widespread was the adoption of OST projects among hacking groups — such as low-level malware gangs, elite financial crime groups, and even nation-state sponsored APTs.
The results were compiled in this interactive map.
The most popular OSTs
Litvak found that OSTs are broadly adopted across the entire cybercrime ecosystem. From famous nation-state groups like DarkHotel to cybercrime operations like TrickBot, many groups deployed tools or libraries that had been initially developed by security researchers but are now regularly used for cybercrime.
“We found [that] the most commonly adopted projects were memory injection libraries and RAT tools,” Litvak said.
“The most popular memory injection tool was the ReflectiveDllInjection library, followed by the MemoryModule library. For RATs [remote access tools], Empire, Powersploit and Quasar were the leading projects.”
The lateral movement category was dominated by Mimikatz — to nobody’s surprise.
UAC bypass libraries were dominated by the UACME library. However, Asian hacking groups appeared to have preferred Win7Elevate, most likely due to Windows 7’s larger regional installbase.
The only OST projects that weren’t popular were those implementing credential-stealing features.
Litvak believed they were not popular because of similar tools provided by black-hats on underground hacking forums, tools that come with superior features, which malware gangs chose to adopt instead of offensive tools provided by the infosec community.
Ways to mitigate broad OST abuse
But Litvak made even a more interesting observation. The Intezer Labs researcher said that OST tools that implemented complex features that required a deeper level of understanding to use were also rarely employed by attackers — even if their offensive hacking capabilities were obvious.
Going on this observation, Litvak argues that security researchers who wish to release offensive hacking tools in the future should also take this approach and introduce complexity into their code, to dissuade threat actors from adopting their toolsets.
If this isn’t possible, Litvak argued that security researchers should at least make their code unique by “sprinkl[ing] the library with special or irregular values” in order to allow easy fingerprinting and detection.
“For example, such an approach was adopted by the author of Mimikatz, where a generated ticket’s lifetime is left to 10 years by default – a highly irregular number,” Litvak said.
The researcher’s talk is also embedded below. A PDF version of his research is available here.