Brave users will now be able to access the decentralized web on desktop and Android as the company behind the...
Fragmentation and aggregation attacks—or frag attacks—refer to a series of design flaws and programming security vulnerabilities affecting Wi-Fi devices. Recent...
Data breaches have become common, and billions of records are stolen worldwide every year. Most of the media coverage of...
Researchers have discovered hundreds of malicious mobile apps that are exploiting interest in cryptocurrency and stocks to steal from victims. ...
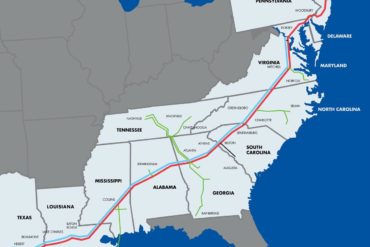
The real-world consequences of a successful cyberattack have been clearly highlighted this week with the closure of one of the...
The FBI and the US Cybersecurity and Infrastructure Security Agency (CISA) have issued a joint advisory in the aftermath of...
After Apple’s recent release of the AirTag for locating misplaced items, security researchers have just succeeded in jailbreaking the new...
Adobe has released a security update to address a vulnerability affecting both Windows and Mac versions of Acrobat DC, Acrobat...
As more private data is stored and shared digitally, researchers are exploring new ways to protect data against attacks from...
“There are two people in a wood, and they run into a bear. The first person gets down on his...
Takeaways: · There are no easy solutions to shoring up U.S. national cyber defenses. · Software supply chains and private...
Colonial Pipeline said Monday its goal is to substantially restore operational service “by the end of the week” following last...