If finding the best VPN for your needs was a simple matter of comparing prices and features, this guide would...
Image: SitePoint, ZDNet, Florian Olivo SitePoint, a website that provides access to a wealth of web development tutorials and books,...
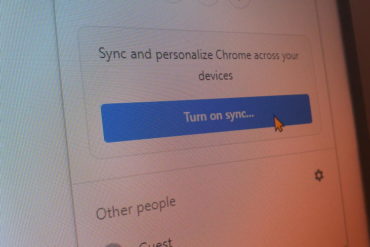
Image: Catalin Cimpanu Threat actors have discovered they can abuse the Google Chrome sync feature to send commands to infected...
Two-factor authentication security keys are now all the rage. If you care about security, then you have at least a...
North Korean hackers have staged an audacious attack targeting cybersecurity researchers, many of whom work to counter hackers from places...
Image: Stormshield, ZDNet, Bophomet Zhang French cyber-security firm Stormshield, a major provider of security services and network security devices to...
Most zoombombing incidents are “inside jobs” according to a new study featuring researchers at Binghamton University, State University of New...
Agent Tesla malware variants are now using new techniques to try and eradicate endpoint antivirus security. On Tuesday, Sophos researchers...
Technology has become a great enabler but it can also be a killer. In this case, it has literally proven...
A Hezbollah-affiliated threat actor known as Lebanese Cedar has been linked to intrusions at telco operators and internet service providers in the...
Stack Overflow, a popular site amongst developers, has revealed more about a week-long breach that it disclosed in May 2019. ...
Citrix employees impacted by a data breach that resulted in the theft of their data have secured a $2.275 million...