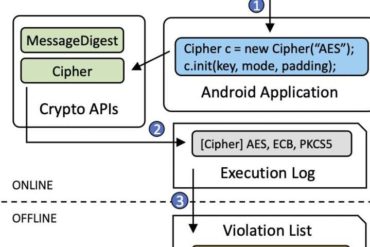
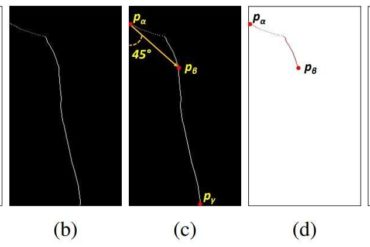
Computer scientists at Columbia Engineering have shown for the first time that it is possible to analyze how thousands of...
Tianfu Cup winners: The 360 Government and Enterprise Security Vulnerability Research Institute Image: Tianfu Cup Many of today’s top software...
Image: ZDNet Verizon is removing the ability to automatically forward incoming emails from a Yahoo inbox to another email address...
The Federal Bureau of Investigation has sent out a security alert warning that threat actors are abusing misconfigured SonarQube applications...
Highly sensitive tax returns, contracts and bank statements were among 75,000 “deleted” files recovered by cybersecurity researchers as part of...
Nearly $1 billion worth of bitcoin with potential ties to the Silk Road online black market is on the move,...
Image: Setyaki Irham, ZDNet More than 23,000 hacked databases have been made available for download on several hacking forums and...
Countless companies around the world see the wildly popular video-conferencing tool Zoom as a savior during this era of quarantine...
Image: Joshua Hoehne The operators of the REvil ransomware strain have “acquired” the source code of the KPOT trojan in...
Screengrab of the GrowDiaries website GrowDiaries, an online community where marijuana growers can blog about their plants and interact with...
All the latest news on the intersection of cybersecurity and the COVID-19 pandemic. Cybersecurity: One in three attacks are coronavirus-related...
SINGAPORE — Southeast Asian e-commerce firm Lazada said it detected a data breach that exposed personal details of many users...