More than $5 billion in bitcoin transactions has been tied to the top ten ransomware variants, according to a report released by the US Treasury on Friday.
The department’s Financial Crimes Enforcement Network (FinCen) and Office of Foreign Assets Control (OFAC) released two reports illustrating just how lucrative cybercrime related to ransomware has become for the gangs behind them. Parts of the report are based on suspicious activity reports (SAR) financial services firms filed to the US government.
FinCen said the total value of suspicious activity reported in ransomware-related SARs during the first six months of 2021 was $590 million, which exceeds the $416 million reported for all of 2020.
“FinCEN analysis of ransomware-related SARs filed during the first half of 2021 indicates that ransomware is an increasing threat to the US financial sector, businesses and the public. The number of ransomware-related SARs filed monthly has grown rapidly, with 635 SARs filed and 458 transactions reported between 1 January 2021 and 30 June 2021, up 30 percent from the total of 487 SARs filed for the entire 2020 calendar year,” the report said.
Through analyzing 177 unique convertible virtual currency wallet addresses used for ransomware-related payments associated with the 10 most commonly-reported ransomware variants in SARs during the review period, the Treasury Department found about $5.2 billion in outgoing bitcoin transactions potentially tied to ransomware payments.
“According to data generated from ransomware-related SARs, the mean average total monthly suspicious amount of ransomware transactions was $66.4 million and the median average was $45 million. FinCEN identified bitcoin as the most common ransomware-related payment method in reported transactions,” the report adds.
FinCen noted that the US dollar figures are based on the value of bitcoin at the time of the transaction and added that the data set “consisted of 2,184 SARs reflecting $1.56 billion in suspicious activity filed between 1 January 2011 and 30 June 2021.”
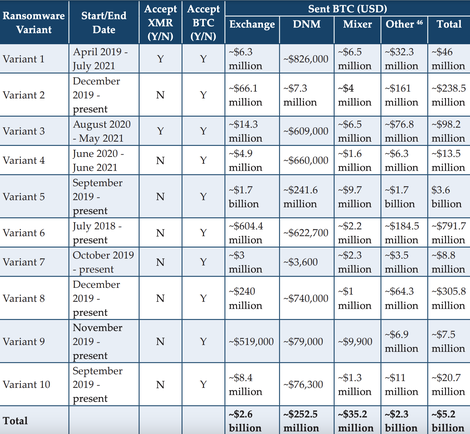
While the report does not say which ransomware variants made more than others, it does list the most commonly reported variants, which were REvil/Sodinokibi, Conti, DarkSide, Avaddon and Phobos. FinCen said it found a total of 68 different ransomware variants.
Ransomware expert and Recorded Future computer emergency response team member Allan Liska told ZDNet that Phobos being in the top five is surprising.
“Phobos tends to fall under the radar and doesn’t get a lot of attention, clearly more focus needs to be placed on it so organizations can better defend themselves against it,” Liska said.
He added that it was interesting to see that FinCen has been tracking ransomware transactions since 2011, meaning they have a lot more experience tracking cryptocurrency transactions than ransomware groups realize.
“I think we all suspected that ransomware attacks were on the rise this year, it is nice to see this confirmed,” he said. “Finally, in just the first 6 months of the year FinCEN identified 68 ransomware variants posted in SAR. Again, I don’t think most people realize just how diverse the ransomware ecosystem is.”
The reports comes one day after the US officials and governments from more than 30 countries finished a two-day summit focused on ransomware and how it can be stopped. The countries pledged further cooperation and specifically mentioned the need to hold cryptocurrency platforms accountable.
Coinciding with the release of the report, FinCen released further guidance effectively threatening the virtual currency industry with penalties if they allow sanctioned people or entities to continue to use their platforms.
“OFAC sanctions compliance requirements apply to the virtual currency industry in the same manner as they do to traditional financial institutions, and there are civil and criminal penalties for failing to comply,” FinCen said on Friday.
The FinCen report also noted that ransomware groups are increasingly using cryptocurrencies like Monero that are popular among those seeking anonymity and have avoided using wallets more than once.
Mixing services are also widely used across the ransomware industry as a way to disrupt tracking experts and decentralized exchanges are being used to convert ransomware payments into other cryptocurrencies.
The report also mentions “chain hopping,” a practice ransomware actors use to change one coin into another at least once before moving the funds to another service or platform.
“This practice allows threat actors to convert illicit BTC proceeds into an AEC like XMR at CVC exchanges or services. Threat actors can then transfer the converted funds to large CVC services and MSBs with lax compliance programs,” FinCen said.


