Google has blocked eight additional ports inside the Chrome web browser in order to prevent a new variation of an attack named NAT Slipstreaming, the company’s engineers announced today.
The original NAT Slipstreaming attack was first disclosed on October 31, 2020, by Samy Kamkar, a well-known security researcher.
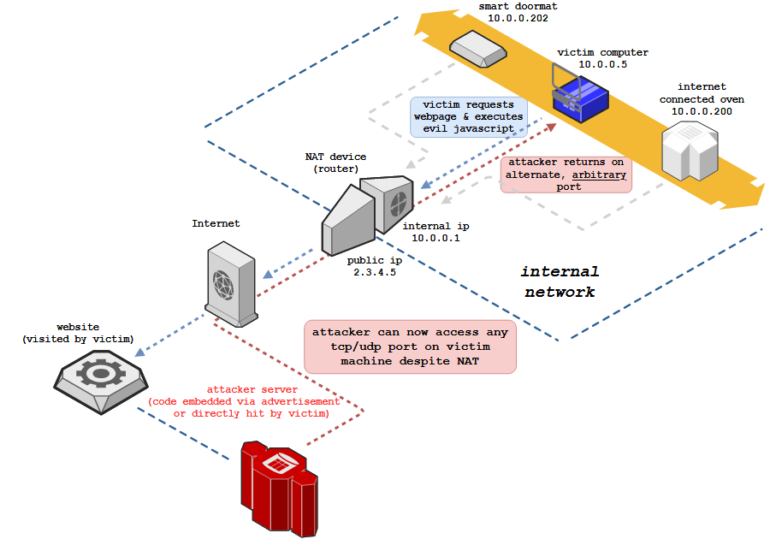
The attack worked by luring users on a malicious website where JavaScript code would establish a connection to a victim’s device directly, bypassing defenses provided by firewalls and network address translation (NAT) tables.
The attacker could abuse this connection to the user’s system to launch attacks on devices located on a victim’s internal network.
The initial version of the NAT Slipstreaming attack abused the Session Initiation Protocol (SIP) protocol to establish these pinhole connections to devices on internal networks via ports 5060 and 5061.
Two weeks after the attack became public, Google responded to Kamkar’s discovery by blocking these two ports in Chrome 87 to prevent attackers from abusing this technique, which the browser maker deemed a severe threat and easy to abuse.
Apple and Mozilla also shipped similar blocks inside Safari and Firefox weeks later.
New NAT Slipstreaming attack variant discovered
But earlier this week, security researchers from IoT security firm announced that they worked with Kamkar to expand the original attack with a new version they named NAT Slipstreaming 2.0.
This new version replaces SIP and piggybacks on the H.323 multimedia protocol to open the same tunnels inside internal networks and bypass firewalls and NAT tables.
Armis researchers said the 2.0 variant of the NAT Slipstreaming attack was just as potent as the first and would have allowed the same class of internet-based attacks on devices normally accessible only from internal LANs.
Ports 69, 137, 161, 1719, 1720, 1723, 6566, 10080 to be blocked
Earlier today, Google said that it would block connections to port 1720, used by the H.323 protocol, but also seven other ports that they believe could also be abused in the same manner for other similar variations of the NAT Slipstreaming attack.
The other seven ports were 69, 137, 161, 1719, 1723, 6566, and 10080.
Any HTTP, HTTPS, or FTP connections via these ports will now fail, Google said today.
According to a Chrome feature status report, the block is already active for any user using a Chrome version of 87.0.4280.117 and later.
It appears updating the list of block ports was done server-side without needing to deliver a separate Chrome update to end-users.
Firefox and Microsoft’s Edge browsers have also deployed a fix for the NAT Slipstreaming 2.0 attack as well. The Firefox patch was delivered in Firefox 85 earlier this week as CVE-2021-23961, while the Edge fix shipped as a fix for CVE-2020-16043.