Members of the Egregor ransomware cartel have been arrested this week in Ukraine, French radio station France Inter reported on Friday, citing law enforcement sources.
The arrests, which have not been formally announced, are the result of a joint investigation between French and Ukrainian police.
Sources in the threat intel community have confirmed the existence of a law enforcement action but declined to comment for the time being.
The names of the suspects have not been released. France Inter said the arrested suspects provided hacking, logistical, and financial support for the Egregor gang.
The Egregor gang, which began operating in September 2020, operates based on a Ransomware-as-a-Service (RaaS) model. They rent access to the actual ransomware strain, but they rely on other cybercrime gangs to orchestrate intrusions into corporate networks and deploy the file-encrypting ransomware.
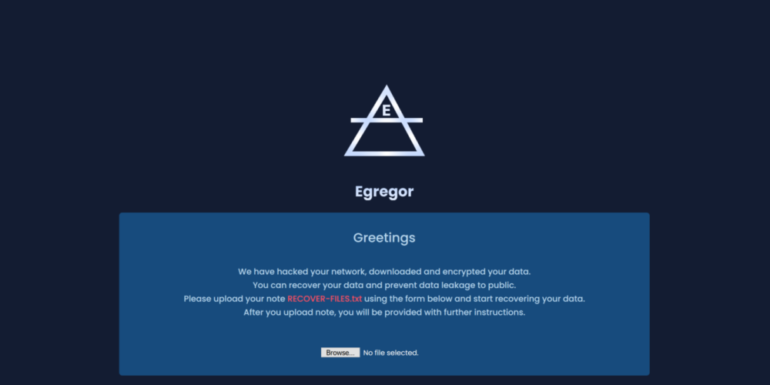
Victims who resist paying the extortion fee are often listed on a so-called “leak site,” in the hopes of shaming them into paying the ransom demand. Victims who don’t pay often have internal documents and files shared on the Egregor leak site as punishment.
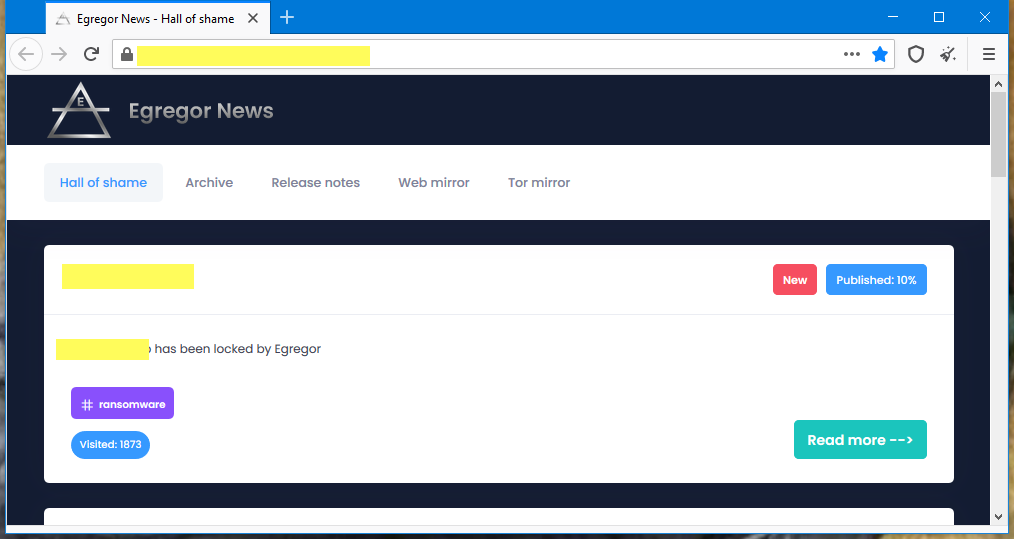

The Egregor ransomware leak site
Image: ZDNet
If victims do pay the ransom demand, the gang which orchestrated the intrusion keeps most of the funds, while the Egregor gang takes a small cut. The gang then launders these profits through the Bitcoin ecosystem via Bitcoin mixing services.
According to the France Inter report, the arrested suspects are believed to some of these “affiliates” (or partners) of the Egregor gang, which help prop up its operations.
France Inter said French authorities got involved in the investigation after several major French companies were hit by Egregor last year, such as game studio Ubisoft and logistics firm Gefco.
An investigation was started last year, and French police, together with “European counterparts,” were able to track down Egregor members and infrastructure to Ukraine.
Egregor leak site down since Friday
While, at the time of writing, details about the law enforcement action are murky, the arrests appear to have had a pretty big impact on Egregor operations.
“Recorded Future has observed that Egregor infrastructure, including their extortion site and command and control (C2) infrastructure, has been offline since at least Friday,” Allan Liska, a security researcher for threat intelligence firm Recorded Future, has told ZDNet in an email.
“While there has been no police banner, as there often would be in this case, it is unusual for ransomware actors as well-resourced as Egregor to have all of their infrastructure go offline at the same time,” he added.
Egregor has made more than 200 public victims
The arrests in Ukraine have hit one of last year’s most active ransomware operations.
While the Egregor RaaS formally launched in September 2020, many security experts believe the Egregor gang is actually the older Maze ransomware group, which began operating in late 2019.
The Maze gang abruptly shut down in September 2020, a few weeks after Egregor began operating. Reports from threat intelligence firms at the time said that the Maze gang had privately notified many of its top “affiliates” to move over to the Egregor RaaS.
Currently, many security researchers believe the Egregor RaaS is an upgraded and rebranded version of the older Maze operation.
“Recorded Future has tracked 206 victims published to the Egregor extortion site and, before the switchover, 263 victims published to the Maze site,” Liska told ZDNet.
“The two variants combined accounted for 34.3% of victims published to all ransomware extortion sites (14.9% Egregor),” Liska said.
A Coveware report published last month confirmed Recorded Future’s assessment, listing Egregor as the second most active ransomware gang for Q4 2020.
However, it is unclear what the damage of this week’s law enforcement action will be on Egregor’s future. Last month, US and Bulgarian authorities disrupted the Netwalker ransomware gang by seizing servers and arresting one of its affiliates, and the RaaS service has been inactive ever since.
A Chainalysis report published at the start of the month listed the Egregor/Maze gang as one of the top 5 earners in the ransomware landscape, with earnings between $40 million and $50 million.
This was confirmed by Liska, who told ZDNet that Egregor’s average ransom demand was around $700,000, making it among the largest ransom demands of any ransomware family.
Maze’s 2020 dox
But a pretty significant event took place last year, in November, when the operators of the REvil (Sodinokibi) ransomware gang (#1 on that Coverware 2020 Q4 ransomware report) claimed to have identified the real identities of the persons behind the Maze service, their rival.
At the time, security analysts considered the REvil stunt as an attempt to sabotage a rival’s public image, but nobody commented on the accuracy of the dox, and ZDNet was told several of them shared the information with law enforcement agencies.