Microsoft has released a one-click mitigation tool as a stop-gap for IT admins who still need to apply security patches to protect their Exchange servers.
Released on Monday, the tool is designed to mitigate the threat posed by four actively-exploited vulnerabilities that have collectively caused havoc for organizations worldwide.
Microsoft released emergency fixes for the critical vulnerabilities on March 2. However, the company estimates that at least 82,000 internet-facing servers are still unpatched and vulnerable to attack.
The company previously released a script on GitHub that administrators could run in order to see if their servers contained indicators of compromise (IOCs) linked to the vulnerabilities. In addition, Microsoft released security updates for out-of-support versions of Exchange Server.
However, after working with clients and partners, Microsoft says there is a need for “a simple, easy to use, automated solution that would meet the needs of customers using both current and out-of-support versions of on-premise Exchange Server.”
See also: Everything you need to know about the Microsoft Exchange Server hack
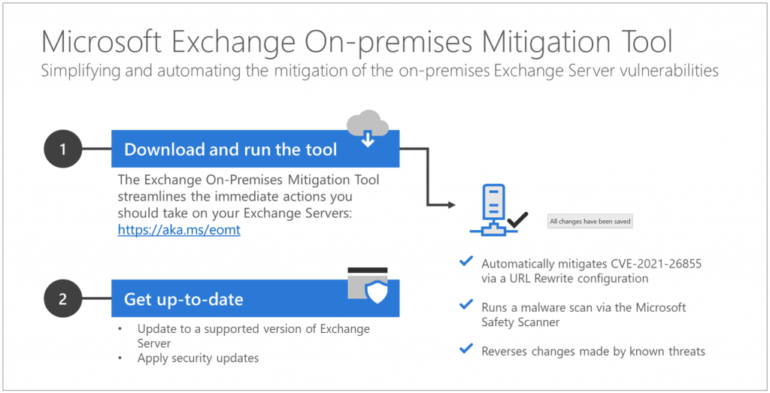
The Microsoft Exchange On-Premises Mitigation Tool has been designed to help customers that might not have security or IT staff on hand to help and has been tested across Exchange Server 2013, 2016, and 2019.
It is important to note the tool is not an alternative to patching but should be considered a means to mitigate the risk of exploit until the update has been applied — which should be completed as quickly as possible.
The tool can be run on existing Exchange servers and includes Microsoft Safety Scanner as well as a URL rewrite mitigation for CVE-2021-26855, which can lead to remote code execution (RCE) attacks if exploited.
“This tool is not a replacement for the Exchange security update but is the fastest and easiest way to mitigate the highest risks to internet-connected, on-premises Exchange Servers prior to patching,” Microsoft says.
In related news this week, Microsoft reportedly began investigating the potential leak of Proof-of-Concept (PoC) attack code supplied privately to cybersecurity partners and vendors ahead of the zero-day public patch release. The company says that no conclusions have yet been drawn over attack spikes related to the vulnerabilities.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0