Pirated (aka nulled) themes and plugins were the most common source of malware infections on WordPress sites in 2020, according to Wordfence, a provider of website application firewall (WAF) solutions for WordPress sites.
The security firm said its malware scanner detected more than 70 million malicious files on more than 1.2 million WordPress sites in 2020.
“Overall, the Wordfence scanner found malware originating from a nulled plugin or theme on 206,000 sites, accounting for over 17% of all infected sites,” the company said on Wednesday.
Of these 206,000 sites, 154,928 were infected with a version of the WP-VCD malware, a WordPress malware strain known for its use of pirated/nulled themes for distribution.
Wordfence said this particular malware operation was so successful last year that it accounted for 13% of all infected sites in 2020.
Over 90 billion malicious login attempts
But WordPress sites also got infected with malware via other means beyond pirated themes. Legitimate sites also got attacked and infected. Other methods through which these sites got hacked included brute-force attacks against login forms and the use of exploit code that takes advantage of unpatched vulnerabilities.
All in all, 2020 was a massive year in terms of brute-force attacks. Wordfence reported seeing more than 90 billion malicious and automated login attempts.
These attacks came from 57 million different IP addresses —most likely part of attack botnets and proxy networks— and amounted to 2,800 malicious login attempts per second against Wordfence customers.
To mitigate these attacks, Wordfence recommended that site owners either deploy a WAF or enable a two-factor authentication solution for their accounts.
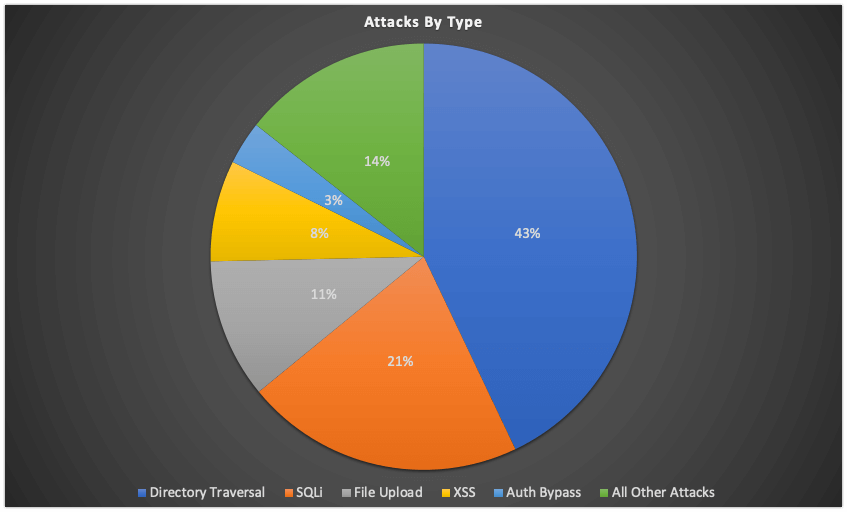
On the vulnerability exploitation front, things were just as bad, with Wordfence reporting more than 4.3 billion exploitation attempts over the past year.
The most common form of vulnerability that attackers exploited last year was “directory traversals,” a type of bug that threat actors try to abuse to read files from WordPress installations (such as wp-config.php) or upload malicious files on a WordPress site.
Other exploitation attempts also relied on SQL injection, remote code execution bugs, cross-site scripting issues, or authentication bypasses, Wordfence said.