Google said today that a quarter of all the zero-day vulnerabilities discovered being exploited in the wild in 2020 could have been avoided if vendors had patched their products correctly.
The company, through its Project Zero security team, said it detected 24 zero-days exploited by attackers in 2020.
Six of these were variations of vulnerabilities disclosed in previous years, where attackers had access to older bug reports so they could study the previous issue and deploy a new exploit version.
“Some of these 0-day exploits only had to change a line or two of code to have a new working 0-day exploit,” Maddie Stone, a member of the Project Zero team, said today in a blog post.
This included zero-days in Chrome, Firefox, Internet Explorer, Safari, and Windows.
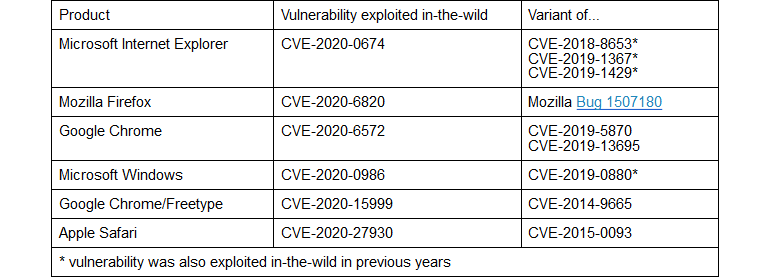

Furthermore, three other zero-days discovered and patched in 2020 could have been exploited in a similar fashion.
Stone said that initial patches for three zero-days —impacting Chrome, Internet Explorer, and Windows— required additional fixes.
If a threat actor would have examined the patches, they could have easily created new exploits and re-weaponized the same vulnerability and continue their attacks.
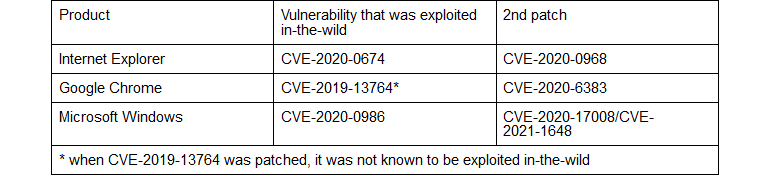

Stone, which also presented her findings at the USENIX Enigma virtual security conference this week, said that this situation could have been avoided if vendors had investigated the root cause of the bugs in greater depth and invested more into the patching process.
The Project Zero researcher urged other security experts to take advantage of when a zero-day vulnerability is exposed and analyze it in greater depth.
Stone argued that zero-days provide a window into an attacker’s mind that defenders should take advantage of and try to learn about the entry vectors an attacker is trying to exploit, determine the vulnerability class, and then deploy comprehensive mitigations.
Stone said this was the primordial reason why the Google Project Zero team was founded years ago, namely to “learn from 0-days exploited in-the-wild in order to make 0-day hard.”



