The new LastPass app combines functionality for business and consumer customers One of the most crucial steps in securing a...
The HSE has now confirmed that a ransom has been sought by the attackers. Getty Images/iStockphoto Ireland’s Health Service Executive...
In the tradition of previous versions, Android 12 will probably launch in less than a week, as Google IO 2021...
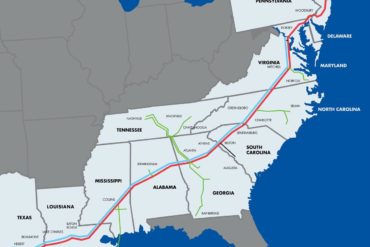
The Colonial Pipeline hack was not the first domino to fall in a world-ending spate of sudden attacks on America’s...
Hacking isn’t necessarily about just having an in-depth knowledge of code: It’s about enjoying a challenge and problem-solving. While understanding...
Brave users will now be able to access the decentralized web on desktop and Android as the company behind the...
Fragmentation and aggregation attacks—or frag attacks—refer to a series of design flaws and programming security vulnerabilities affecting Wi-Fi devices. Recent...
Data breaches have become common, and billions of records are stolen worldwide every year. Most of the media coverage of...
Researchers have discovered hundreds of malicious mobile apps that are exploiting interest in cryptocurrency and stocks to steal from victims. ...
The real-world consequences of a successful cyberattack have been clearly highlighted this week with the closure of one of the...
The FBI and the US Cybersecurity and Infrastructure Security Agency (CISA) have issued a joint advisory in the aftermath of...
After Apple’s recent release of the AirTag for locating misplaced items, security researchers have just succeeded in jailbreaking the new...