Adobe has released a security update to address a vulnerability affecting both Windows and Mac versions of Acrobat DC, Acrobat...
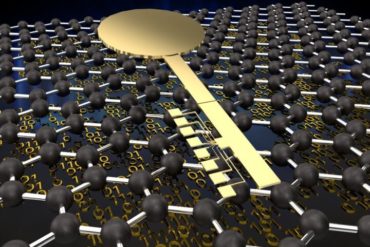
As more private data is stored and shared digitally, researchers are exploring new ways to protect data against attacks from...
“There are two people in a wood, and they run into a bear. The first person gets down on his...
Takeaways: · There are no easy solutions to shoring up U.S. national cyber defenses. · Software supply chains and private...
Colonial Pipeline said Monday its goal is to substantially restore operational service “by the end of the week” following last...
The Department of Computer Science and Center for Information Technology Policy at Princeton University has conducted a study and released...
The DarkSide hacker gang that is reportedly responsible for the devastating Colonial Pipeline attack this weekend is a relatively new...
Voice ID was introduced in 2016 to increase the security of bank transactions carried out over the phone. Francesco...
Research from James Cook University shows increasingly complex website password restrictions often leave users frustrated and lead to poor password...
Good people need encryption too. Getty Images/iStockphoto How do you tell your best friend that her boyfriend has all the...
Upgrading to a new phone is always a satisfying feeling, but experts have warned that changing your phone number could...
Check Point Research (CPR) has identified a security flaw in the Qualcomm chip of the mobile station modems (MSM) used...