Have you ever seen a dark shape out of the corner of your eye and thought it was a person,...
Proponents of artificial intelligence say its potential is limitless. But cyber scammers could also use it to their advantage. Analysts...
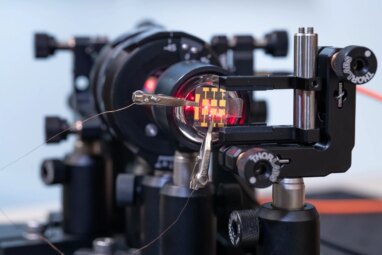
Digital information exchange can be safer, cheaper and more environmentally friendly with the help of a new type of random...
White House officials concerned by AI chatbots’ potential for societal harm and the Silicon Valley powerhouses rushing them to market...
A team of computer security experts have developed a set of recommendations to help defend against “thermal attacks” which can...
While augmented reality (AR) and virtual reality (VR) are envisioned as the next iteration of the internet immersing us in...
Two out of five homes worldwide have at least one smart device that is vulnerable to cyber-attacks. Soon, that new...
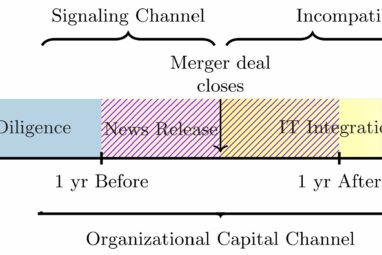
The period during and after hospital mergers and acquisitions is an especially vulnerable time for patient data when the chance...
A newly discovered vulnerability in text messaging may enable attackers to trace your location, according to Northeastern Ph.D. student Evangelos...
If you find the computer security guidelines you get at work confusing and not very useful, you’re not alone. A...
Have you ever been compelled to enter sensitive payment data on the website of an unknown merchant? Would you be...
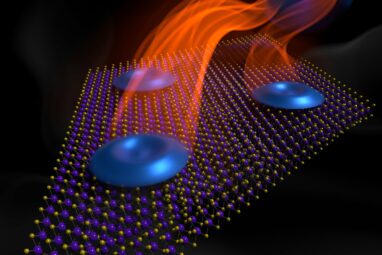
A savvy hacker can obtain secret information, such as a password, by observing a computer program’s behavior, like how much...