You have just returned home after a long day at work and are about to sit down for dinner when...
ChatGPT’s explosive growth has been breathtaking. Barely two months after its introduction last fall, 100 million users had tapped into...
A cybersecurity technique that shuffles network addresses like a blackjack dealer shuffles playing cards could effectively befuddle hackers gambling for...
Chinese scientists have successfully implemented a new way of quantum key distribution (QKD) which can boost the speed of intercity...
Privacy preservation is the most challenging issue for data collection. Even if the data is encrypted, metadata, such as users’...
Personal emails linked to 235 million Twitter accounts hacked some time ago have been exposed according to Israeli security researcher...
IMDEA Software researchers Gibran Gómez, Pedro Moreno-Sánchez and Juan Caballero have created an open-source automated tool to track the financial...
It is common to hear news reports about large data breaches, but what happens once your personal data is stolen?...
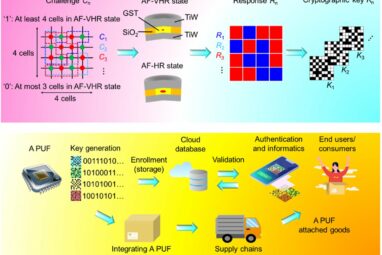
In the digital era and moving towards quantum computing, protecting data against hack attacks is one of our biggest challenges—and...
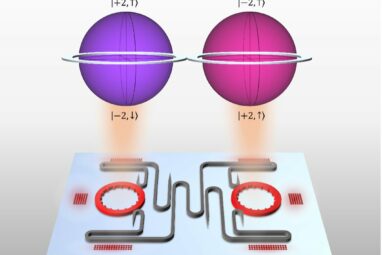
Researchers at Penn Engineering have created a chip that outstrips the security and robustness of existing quantum communications hardware. Their...
As more and more data are being shared and stored digitally, the number of data breaches taking place around the...
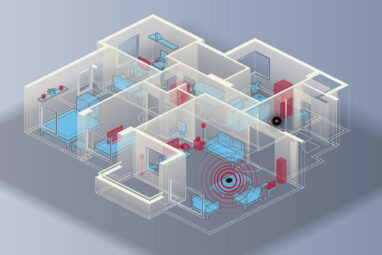
Machine learning programs mean even encrypted information can give cybercriminals insight into your daily habits. Smart technology claims to make...