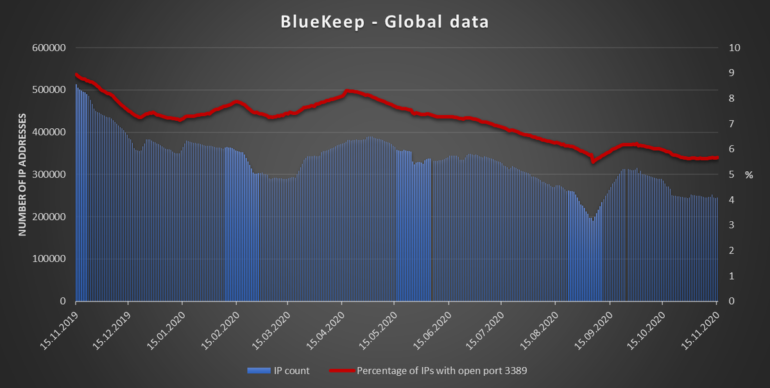
A year and a half after Microsoft disclosed the BlueKeep vulnerability impacting the Windows RDP service, more than 245,000 Windows systems still remain unpatched and vulnerable to attacks.
The number represents around 25% of the 950,000 systems that were initially discovered to be vulnerable to BlueKeep attacks during a first scan in May 2019.
Similarly, more than 103,000 Windows systems also remain vulnerable to SMBGhost, a vulnerability in the Server Message Block v3 (SMB) protocol that ships with recent versions of Windows, disclosed in March 2020.
Both vulnerabilities allow attackers to take over Windows systems remotely and are considered some of the most severe bugs disclosed in Windows over the past few years.
However, despite their severity, many systems have remained unpatched, according to research compiled over the past few weeks by SANS ISC handler Jan Kopriva [1, 2].
Kopriva says that BlueKeep and SMBGhost aren’t the only major remotely-exploitable vulnerabilities that still have a strong presence online these days, exposing systems to attacks.
According to the Czech security researcher, there are still millions of internet-accessible systems that administrators have failed to patch and are vulnerable to remote takeovers. These include systems like IIS servers, Exim email agents, OpenSSL clients, and WordPress sites.
CVE
PRODUCT
UNPATCHED SYSTEMS
CVSSv3 CVE-2019-0211
Apache web server
3,357,835
7.8 CVE-2019-12525 Squid
1,219,716
9.8 CVE-2015-1635
Microsoft IIS
374,113
10 CVE-2019-13917
Exim
268,409
9.8 CVE-2019-10149 (Return of the WIZard)
Exim
264,655
9.8 CVE-2019-0708 (BlueKeep)
Windows RDP
246,869
9.8 CVE-2014-0160 (Heartbleed)
OpenSSL
204,878
7.5 CVE-2020-0796 (SMBGhost)
Windows SMB
103,000
10
CVE-2019-9787 WordPress
83,951
8.8 CVE-2019-12815 ProFTPD
80,434
9.8 CVE-2018-6789 Exim
76,344
9.8
The causes why these systems have been left unpatched remain unknown, but even recent warnings from US government cyber-security agencies have not helped.
This includes two warnings from the US National Security Agency (NSA), one issued in May (for the Exim bug CVE-2019-10149 that was exploited by Russian state hackers), and a second in October (for the BlueKeep bug that was exploited by Chinese state hackers).
Yet, despite these warnings, there are still more than 268,000 Exim servers unpatched for the Exim bug and more than 245,000 unpatched for BlueKeep.
Kopriva says the numbers show that “even very well-known vulnerabilities are sometimes left unpatched for years on end.”
“Given how dangerous and well known BlueKeep is, it rather begs the question of how many other, less well-known critical vulnerabilities are still left unpatched on a similar number of systems,” Kopriva also adds.