Hackers are resetting passwords for admin accounts on WordPress sites using a zero-day vulnerability in a popular WordPress plugin installed on more than 500,000 sites.
The zero-day was used in attacks over the past weeks and was patched on Monday.
It impacts Easy WP SMTP, a plugin that lets site owners configure the SMTP settings for their website’s outgoing emails.
According to the team at Ninja Technologies Network (NinTechNet), Easy WP SMTP 1.4.2 and older versions of the plugin contain a feature that creates debug logs for all emails sent by the site, which it then stores in its installation folder.
“The plugin’s folder doesn’t have any index.html file, hence, on servers that have directory listing enabled, hackers can find and view the log,” said NinTechNet’s Jerome Bruandet.
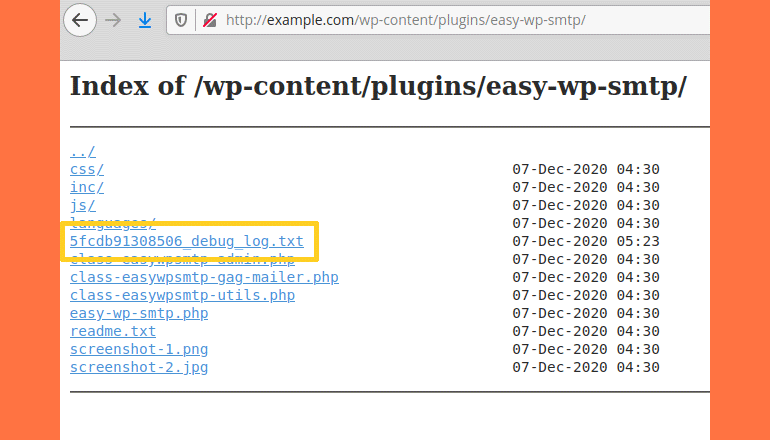

Bruandet says that on sites running vulnerable versions of this plugin, hackers have been carrying out automated attacks to identify the admin account and then initiate a password reset.
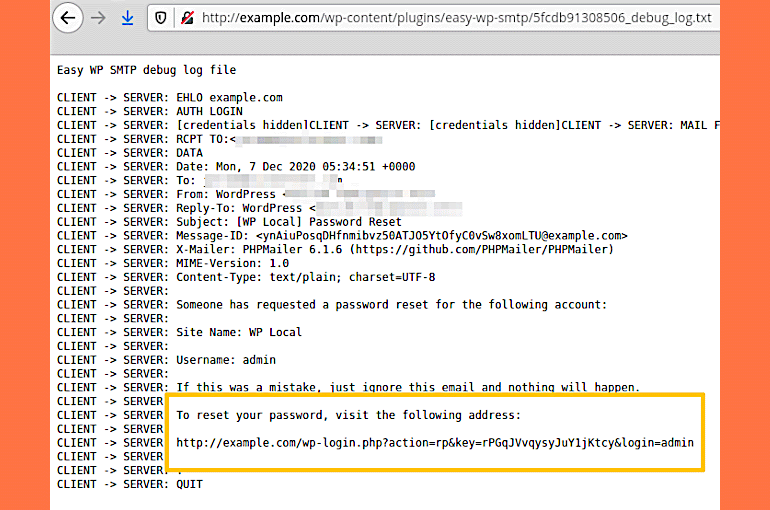
Since a password reset involves sending an email with the password reset link to the admin account, this email is also recorded in the Easy WP SMTP debug log.
All attackers have to do is access the debug log after the password reset, grab the reset link, and take over the site’s admin account.

“This vulnerability is currently exploited, make sure to update as soon as possible to the latest version,” Bruandet warned earlier this week on Monday.
The plugin’s developers have fixed this issue by moving the plugin’s debug log into the WordPress logs folder, where it’s better protected. The version where this bug was fixed is Easy WP SMTP 1.4.4, according to the plugin’s changelog.
This marks the second zero-day discovered in this very popular plugin. A first zero-day was discovered being abused in the wild in March 2019, when hackers used a Easy WP SMTP vulnerability to enable user registration and then created backdoor admin accounts.
The good news is that compared to March 2019, today, the WordPress CMS has received a built-in auto-update function for themes and plugins.
Added in August 2020, with the release of WordPress 5.5, if enabled, this feature will allow plugins to always run on the latest version by updating themselves, instead of waiting for an admin’s button press.
However, it is currently unclear how many WordPress sites have this feature enabled and how many of the 500,000+ WordPress sites are currently running the latest (patched) Easy WP SMTP version.
According to WordPress.org stats, the number isn’t that high, meaning that many sites remain vulnerable to attacks.