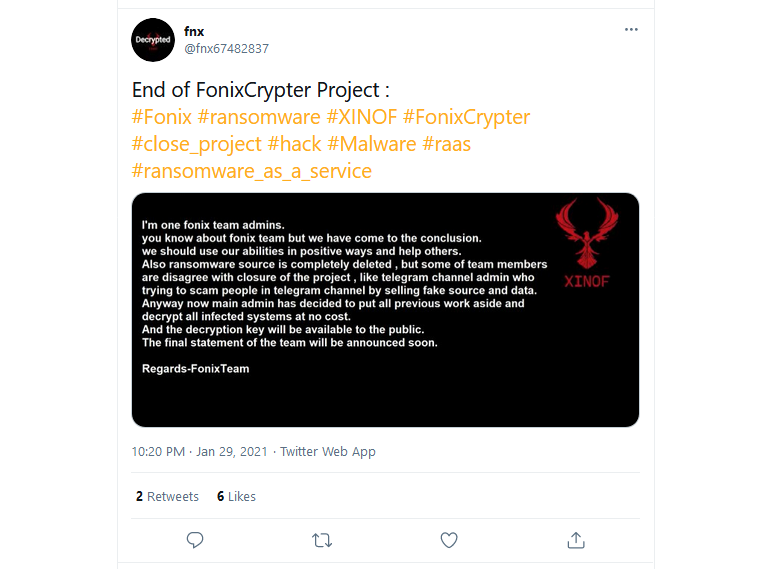
The cybercrime group behind the FonixCrypter ransomware has announced today on Twitter that they’ve deleted the ransomware’s source code and plan to shut down their operation.
As a gesture of goodwill towards past victims, the FonixCrypter gang has also released a package containing a decryption tool, how-to instructions, and the ransomware’s master decryption key.
These files can be used by former infected users to decrypt and recover their files for free, without needing to pay for a decryption key.
Allan Liska, a security researcher for threat intelligence firm Recorded Future, has tested the decrypter at ZDNet’s request earlier today and verified that the FonixCrypter app, instructions, and master key work as advertised.
“The decryption key provided by the actors behind the Fonix ransomware appears to be legitimate, thought it requires each file to be decrypted individually,” Liska told ZDNet.
“The important thing is that they included the master key, which should enable someone to build a much better decryption tool,” he added.
A better decrypter is currently in the works at Emsisoft and is expected to be released next week, Michael Gillespie, an Emsisoft security researcher specialized in breaking ransomware encryption, has told ZDNet earlier today in an online chat. Users are advised to wait for the Emsisoft decrypter rather than use the one provided by the FonixCrypter gang, which may easily contain other malware, such as backdoors, that victims might end up installing on their systems.
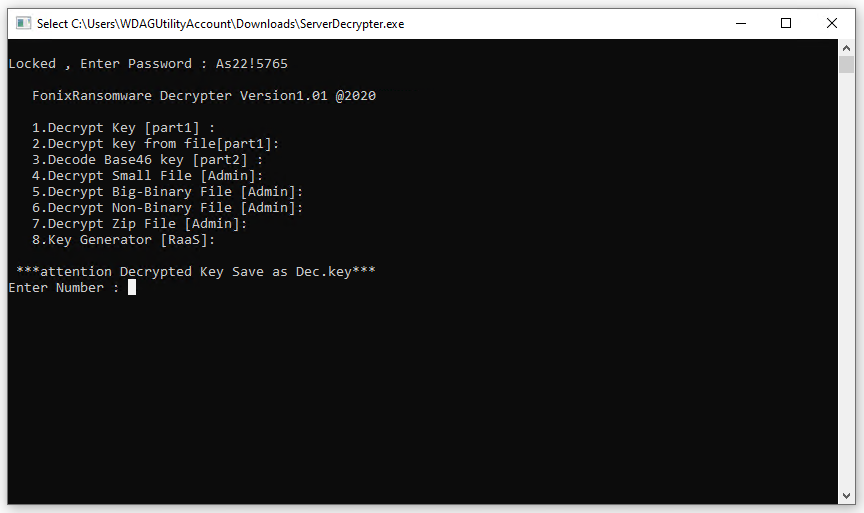

The decryption utility released today by the FonixCrypter gang
Image: ZDNet
Prior to shutting down today, the FonixCrypter ransomware gang has been active since at least June 2020, according to Andrew Ivanov, a Russian security researcher who’s been tracking ransomware strains on his personal blog for the past four years.
Ivanov’s FonixCrypter blog entry shows a history of constant updates to the FonixCrypt code, with at least seven different FonixCrypt variants being released last year.
While the ransomware’s source code might not have been top-notch, the ransomware worked and was deployed in the wild last year, making victims all over the globe.
Currently, all signs point to the fact that the FonixCrypter gang is serious about their plans to shut down. Liska said the FonixCrypter gang had removed today its Telegram channel where they usually advertised the ransomware to other criminal groups, but the Recorded Future analyst also pointed out that the group also announced plans to open a new channel in the near future.
The FonixCrypter gang, however, did not specify if this new Telegram channel will focus on providing a new and improved ransomware strain. According to a message posted on Twitter, the group claims they plan to move away from ransomware and use their abilities in “positive ways.” Whatever that means.