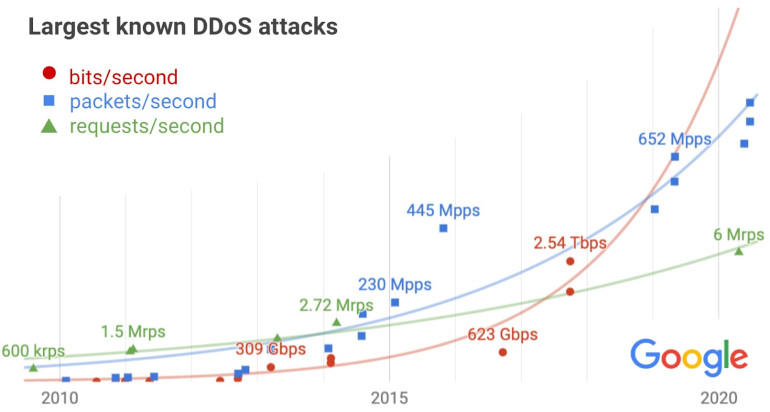
The Google Cloud team revealed today a previously undisclosed DDoS attack that targeted Google service back in September 2017 and which clocked at 2.54 Tbps, making it the largest DDoS attack recorded to date.
In a separate report published at the same time, the Google Threat Threat Analysis Group (TAG), the Google security team that analyzes high-end threat groups, said the attack was carried out by a state-sponsored threat actor.
TAG researchers said the attack came from China, having originated from within the network of four Chinese internet service providers (ASNs 4134, 4837, 58453, and 9394).
Damian Menscher, a Security Reliability Engineer for Google Cloud, said the 2.54 Tbps peak was “the culmination of a six-month campaign” that utilized multiple methods of attacks to hammer Google’s server infrastructure.
Menscher didn’t reveal which services were targeted.
“The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us,” Menscher said.
“This demonstrates the volumes a well-resourced attacker can achieve: This was four times larger than the record-breaking 623 Gbps attack from the Mirai botnet a year earlier [in 2016].”
Furthermore, this attack is also larger than the 2.3 Tbps DDoS attack that targeted Amazon’s AWS infrastructure in February this year.
Despite keeping the attack secret for three years, Google disclosed the incident today for different reasons.
The Google TAG team wanted to raise awareness to an increasing trend of nation-state hacker groups abusing DDoS attacks to disrupt targets.
The Google Cloud team also wanted to raise awareness of the fact that DDoS attacks would intensify in the coming years, as internet bandwidth also increases.
In a report published on Wednesday, data center company Equinix predicted an increase of roughly 45% (~16,300+ Tbps) in global interconnection bandwidth by 2023.