As forensic evidence is slowly being unearthed in the aftermath of the SolarWinds supply chain attack, security researchers have discovered a second threat actor that has exploited the SolarWinds software to plant malware on corporate and government networks.
Details about this second threat actor are still scarce, but security researchers don’t believe this second entity is related to the suspected Russian government-backed hackers who breached SolarWinds to insert malware inside its official Orion app.
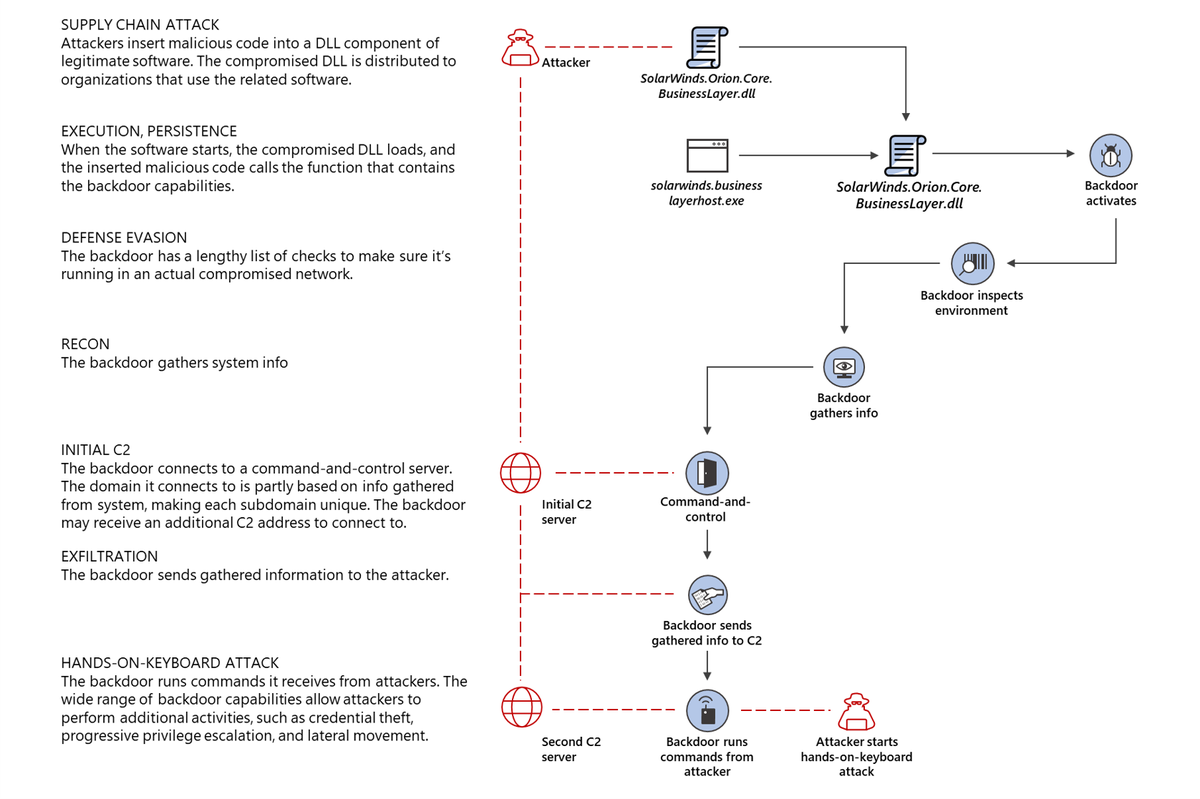
The malware used in the original attack, codenamed Sunburst (or Solorigate), was delivered to SolarWinds customers as a boobytrapped update for the Orion app.
On infected networks, the malware would ping its creators and then download a second stage-phase backdoor trojan named Teardrop that allowed attackers to start a hands-on-keyboard session, also known as a human-operated attack.

But in the first few days following the public disclosure of the SolarWinds hack, initial reports mentioned two second-stage payloads.
Reports from Guidepoint, Symantec, and Palo Alto Networks detailed how attackers were also planting a .NET web shell named Supernova.
Security researchers believed attackers were using the Supernova web shell to download, compile, and execute a malicious Powershell script (which some have named CosmicGale).
However, in follow-up analysis from Microsoft’s security teams, it’s been now clarified that the Supernova web shell was not part of the original attack chain.
Companies that find Supernova on their SolarWinds installations need to treat this incident as a separate attack.
According to a post on GitHub by Microsoft security analyst Nick Carr, the Supernova web shell appears to be planted on SolarWinds Orion installations that have been left exposed online and have been left unptched and vulnerable to a vulnerability tracked as CVE-2019-8917.
This is excellent analysis of a webshell!
However, SUPERNOVA & COSMICGALE are unrelated to this intrusion campaign.
You should definitely investigate them separately bc they are interesting – but don’t let it distract from the SUNBURST intrusions.
Details: https://t.co/6FA6VlABV3— Nick Carr (@ItsReallyNick) December 17, 2020
The confusion that Supernova was related to the Sunburst+Teardrop attack chain came from the fact that just like Sunburst, Supernova was disguised as a DLL for the Orion app — with Sunburst being hidden inside the SolarWinds.Orion.Core.BusinessLayer.dll file and Supernova inside App_Web_logoimagehandler.ashx.b6031896.dll.
But in an analysis posted late Friday, on December 18, Microsoft said that unlike the Sunburst DLL, the Supernova DLL was not signed with a legitimate SolarWinds digital certificate.
The fact that Supernova was not signed was deemed extremely uncharacteristic for the attackers, who until then showed a very high degree of sophistication and attention to detail in their operation.
This included spending months undetected in SolarWinds’ internal network, adding dummy buffer code to the Orion app in advance disguise the addition of malicious code later, and disguising their malicious code to make it look like SolarWinds devs wrote it themselves.
All of this seemed like too much of a glaring mistake that the initial attackers wouldn’t have done, and, as a result, Microsoft believes that this malware is unrelated to the original SolarWinds supply chain attack.



