A ransomware gang has donated a part of the ransom demands it extorted from victims to charity organizations.
Current recipients include Children International, a non-profit for sponsoring children in extreme poverty, and The Water Project, a non-profit aiming to provide access to clean and reliable water across sub-Saharan Africa.
Each organization received 0.88 bitcoin (~$10,000) last week, according to transactions on the Bitcoin blockchain [1, 2].
The sender was a ransomware group going by the name of Darkside.
Active since August 2020, the Darkside group is a classic “big game hunter,” meaning it specifically goes after large corporate networks, encrypts their data, and asks huge ransom demands in the realm of millions of US dollars.
If victims don’t pay, the Darkside group leaks their data online, on a portal they are operating on the dark web.
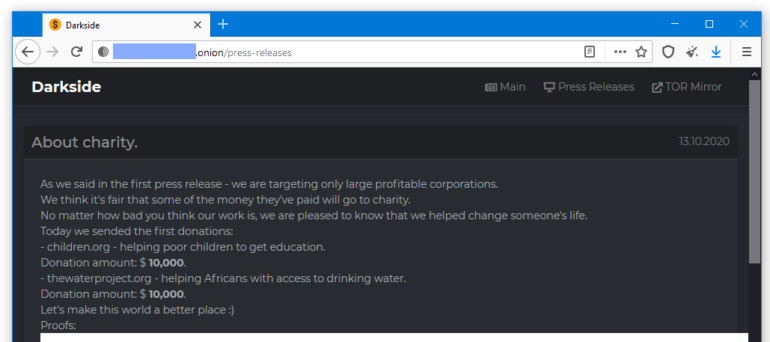
“As we said in the first press release – we are targeting only large profitable corporations,” the Darkside group wrote in a page on their dark web portal, published on Monday.
“We think it’s fair that some of the money they’ve paid will go to charity. No matter how bad you think our work is, we are pleased to know that we helped change someone’s life,” the group also added; before posting proof of their two donations.


This “press release,” as the group calls it, comes after a similar one published online in August, where the group promised not to encrypt files belonging to hospitals, schools, universities, non-profits, and the government sector.
If they kept their promise is currently impossible to tell. Other ransomware gangs have also promised not to attack the healthcare sector at the start of the COVID-19 pandemic, but eventually went back on their word.
Further, the Darkside group isn’t the first cybercrime gang to donate money to charities and non-profits.
In 2016, a hacker group going by the name of Phineas Fisher claimed they hacked a bank and donated the money to the Rojava autonomous Syrian province.
In 2018, the GandCrab ransomware gang released free decryption keys for victims located in war-torn Syria.
The GandCrab gang also added an exemption into their code that would not encrypt files for victims located in this country. Ironically, this unconventional exemption for Syrian victims is what helped security researchers tie the group to the REvil ransomware when the GandCrab group shut down and attempted to start a new operation under a new name (REvil, or Sodinokibi).