Helicopter maker Kopter has fallen victim to a ransomware attack after hackers breached its internal network and encrypted the company’s files.
After Kopter refused to engage with the hackers, the ransomware gang has published on Friday some of the company’s files on the internet.
Many ransomware groups upload and share victim data on special “leak sites” as part of their tactics to put pressure on the hacked companies to either have them come to the negotiation table or force them into paying huge ransom demands.
LockBit ransomware gang takes credit
The Kopter data has been published on a blog hosted on the dark web and operated by the LockBit ransomware gang. Files shared on this site include business documents, internal projects, and various aerospace and defense industry standards.
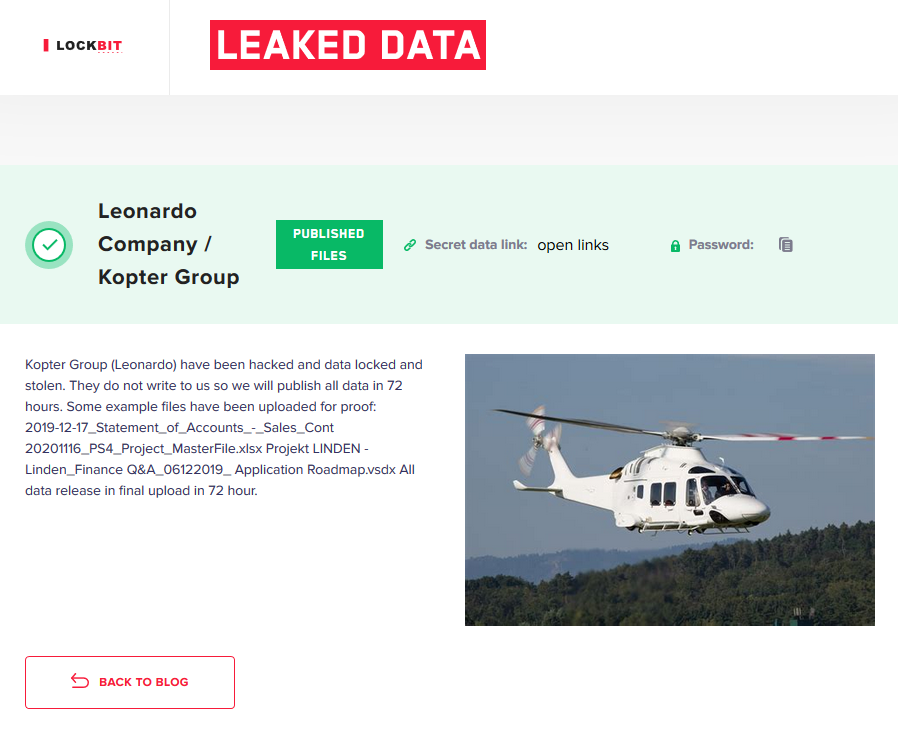

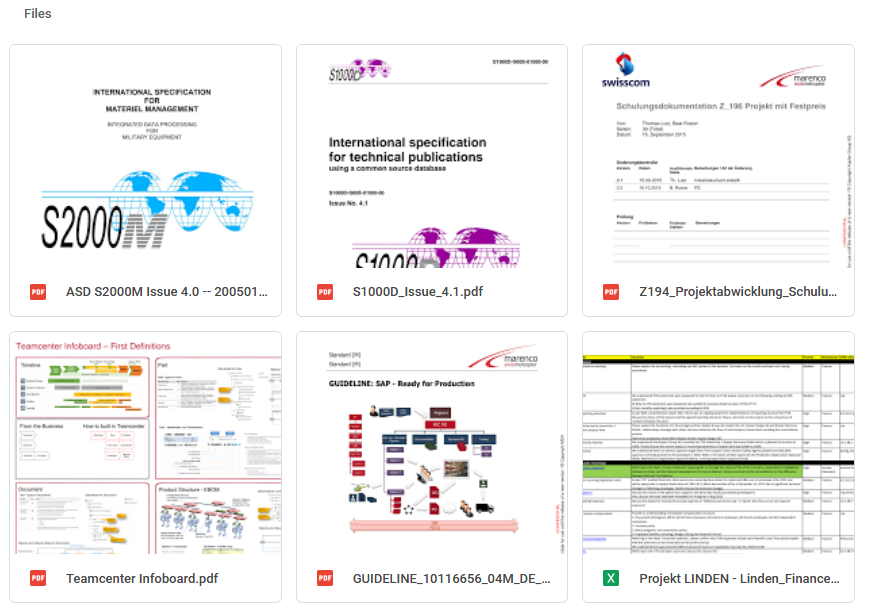

In an email, the operators of the LockBit ransomware told ZDNet that they breached Kopter’s network last week by exploiting a VPN appliance that used a weak password and did not have two-factor authentication (2FA) enabled.
The LockBit gang also said they operate a web portal on the dark web where they show details to hacked companies about the attack, including a ransom demand. LockBit operators said someone from Kopter accessed the ransom page, but the company did not engage with them in a chat window provided to hacked companies.
Kopter has not publicly disclosed a security breach on its website or via business wires.
A Kopter spokesperson did not return an email seeking comment on the ransomware attack. Phone calls made on Friday also remained unanswered.
The Switzerland-based company was founded in 2007 and is known for its line of small and medium-class civilian helicopters.
In January 2020, Italian aerospace and defense company Leonardo acquired Kopter for an undisclosed sum.