When a security vulnerability in the Cellmate chastity cage brought a new meaning to being locked up last year, you would have hoped other sex toy vendors would have heeded the warning.
However, it seems that smart sex toys are still anything but intelligent when it comes to personal privacy, with some of the most popular toys on the market still lagging behind when it comes to basic security measures.
Smart sex toys are equipped with a variety of features: internet connectivity, remote control, Bluetooth links, video, messaging, apps for measuring and monitoring responses, and more.
However, there are concerns that in the rush to offer more and more connectivity options, sex toys could be leaving users open to “data breaches and attacks, both cyber and physical.”
On Thursday, researchers from ESET published a whitepaper exploring the security posture of these devices: in particular, two popular products from WOW Tech Group and Lovense.
The first subject is We-Vibe Jive, a Bluetooth-enabled female vibrator that can be connected to the We-Connect mobile app for controlling vibrations and handing over control to a partner.
The second product examined was the Lovense Max, a male masturbation sleeve. This device, too, is able to connect to a mobile app, the Lovense Remote, which is described as having features including “local remote control, long-distance control, music-based vibrations, creating and sharing patterns, sending patterns syncing two toys together, [and] sound-activated vibrations.”
For both the Jive and Max, the researchers examined the security between the devices and Google Play Store apps. Both devices use Bluetooth Low Energy (BLE) technologies, which while useful to keep power consumption low, are not necessarily very secure.
The We-Vibe Jive keeps user data collection to a minimum but used the least secure of BLE pairing options — a temporary code used to link up the Jive is set to zero. As a result, the device was subject to Man-in-The-Middle (MitM) attacks, in which any unauthenticated smartphone or PC could connect to a physical device.
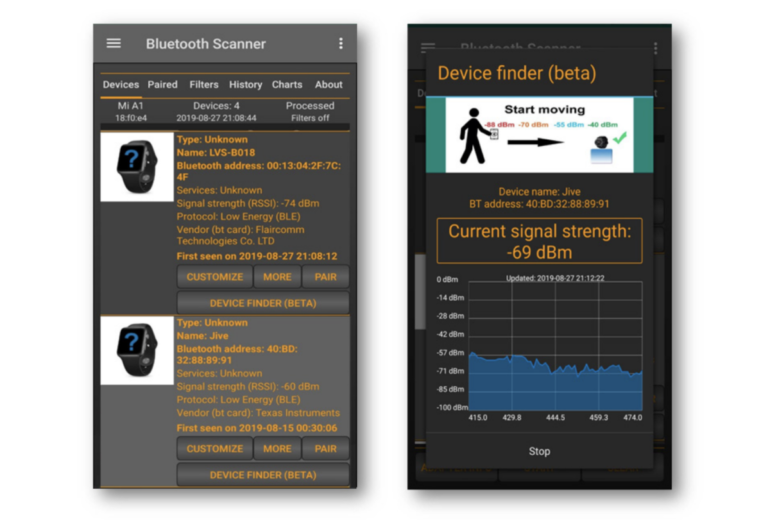
As a wearable product, it is possible that users will wear it while out-and-about — and the Jive broadcasted its presence “continually” to establish a connection, ESET says.
“Anyone can use a simple Bluetooth scanner to find any such devices in their vicinity,” the researchers say. “[Jive] is designed for the user to be able to wear it as they go about their day — at restaurants, parties, hotels, or in any other public location. In these situations, an attacker could identify the device and use the device’s signal strength as a compass to guide them and gradually get closer until they find the exact person wearing it.”
Multimedia files can be shared between We-Connect users during chat sessions and while they are deleted as soon as messaging ends — an effort to protect what is likely to be intimate content — the metadata remained. In other words, whenever a file is sent, so is a user’s device data and geolocation, which did not vanish.
Another privacy issue of note was a lack of brute-force protection on app PIN access attempts.
The Lovense Max contained a number of “controversial” design choices, ESET says, which could compromise the “confidentiality of intimate images one user shares with another.”
Among these was the option to download and forward on images to third-parties without the knowledge or consent of the original owner, as well as reliance on just HTTPS and not end-to-end encryption in image transfers.
In addition, while users often create fantasy names, the Lovense Max app used their email addresses — stored in plaintext — to facilitate messaging. Tokens, which can be shared publicly, were also generated using few numbers and were active longer than claimed, and, therefore, could be susceptible to brute-force attacks leading to information disclosure.
Lovense Max also did not authenticate BLE connections and so was vulnerable to the same MiTM attacks as Jive. A lack of certificate pinning in firmware updates was also noted in the report.
“The consequences of data breaches in this sphere can be particularly disastrous when the information leaked concerns sexual orientation, sexual behaviors, and intimate photos,” ESET says. “As the sex toy market advances, manufacturers must keep cybersecurity top of mind, as everyone has a right to use safe and secure technology.”
ESET disclosed the vulnerabilities to WOW Tech Group and Lovense in June 2020 and the security issues were acknowledged within several weeks. Lovense patched all of the bugs reported by July 27, whereas We-Connect version 4.4.1, pushed in August, has resolved the PIN and metadata issues. Lovense is now working on enhanced privacy features.
“We take reports and findings by external sources about possible vulnerabilities very seriously,” WOW Tech Group said in a statement. “We had the opportunity to patch the vulnerabilities before the presentation and the publication of this report and have since updated the We-Connect App to fix the problems that are described in this report.”
“Putting the health and safety of our users first, Lovense works tirelessly to improve the cybersecurity of its products and software solutions,” Lovense commented. “Thanks to productive cooperation with ESET Research Lab, we were able to detect some vulnerabilities which have been successfully eliminated. Lovense will continue to cooperate with cybersecurity testers to ensure maximum security for all users of Lovense products.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0