With electric vehicles becoming more common, the risks and hazards of a cyber attack on electric vehicle charging equipment and...
Websites and companies that rely on OpenSSL should patch their systems as soon as possible. The developer of Open SSL,...
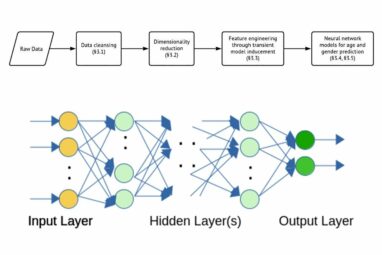
A research team at Illinois Institute of Technology has extracted personal information, specifically protected characteristics like age and gender, from...
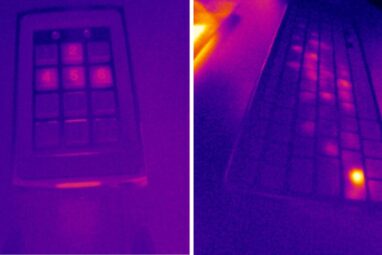
Computer security experts have developed a system capable of guessing computer and smartphone users’ passwords in seconds by analyzing the...
Uber said Thursday that it reached out to law enforcement after a hacker apparently breached its network. A security engineer...
A lot of hurdles remain before the emerging technology of self-driving personal and commercial vehicles is common, but transportation researchers...
Did Twitter ignore basic security measures? A cybersecurity expert explains a whistleblower’s claims
Twitter’s former security chief, Peiter “Mudge” Zatko, filed a whistleblower complaint with the Securities and Exchange Commission in July 2022,...
The pandemic gave people a lot more time with their dogs and cats, but return to the office has disrupted...
An encryption tool co-created by a University of Cincinnati math professor will soon safeguard the telecommunications, online retail and banking...
The software that runs John Deere tractors was successfully “jailbroken” at this year’s DEF CON hacker convention, enabling farmers to...
Apple disclosed serious security vulnerabilities for iPhones, iPads and Macs that could potentially allow attackers to take complete control of...
A component of computer processors that connects different parts of the chip can be exploited by malicious agents who seek...