When a person applies to work for Uber or Lyft they must fill out several online forms detailing important information,...
Smart homes are intended to make life easier, but logging into individual devices is often still an onerous task. Researchers...
Hackers commonly bypass Microsoft Windows kernel protections to enable cheating in competitive online games, new research shows. Academics at the...
Artificial intelligence can help people process and comprehend large amounts of data with precision, but the modern image recognition platforms...
Screen readers, voice-to-text, and other accessibility features have enabled people with disabilities to use smartphones. Yet these same features make...
The Internet Archive, an online repository of web pages, was offline Thursday after its founder confirmed a major cyberattack that...
Browser extensions, the software add-ons that help users customize and enhance their web browsers, are wildly popular. Some of the...
Emerging self-driving vehicle networks that collaborate and communicate with each other or infrastructure to make decisions are vulnerable to data...
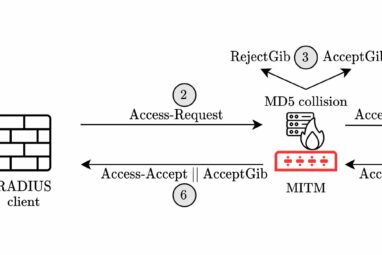
A widely used security protocol that dates back to the days of dial-up internet has vulnerabilities that could expose large...
Smartwatches might be good for tracking steps and heart rates, but they can also offer hackers a wealth of personal...
EPFL researchers in computer and communication sciences are hacking and fixing Android phones before malicious hackers do. They uncovered 31...
From data breaches to widespread systemic shutdowns, cyberattacks like the 2024 Fulton County (Georgia) government attack now occur as regularly...