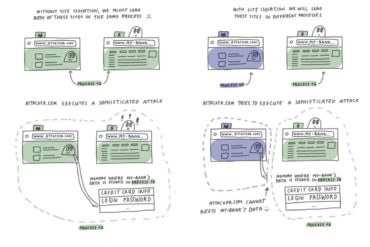
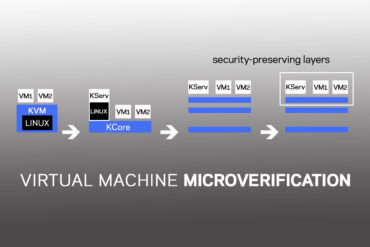
The trek towards the holy grail of cybersecurity—a user-friendly computing environment where the guarantee of security is as strong as...
Image: Mozilla Mozilla is currently testing a new security architecture for its Firefox browser in nightly and beta channels that...
Whenever you buy something on Amazon, your customer data is automatically updated and stored on thousands of virtual machines in...
I know it’s still hard for some of you to wrap your minds around it, but Microsoft really does support...
Facebook’s WhatsApp is changing its privacy policy on Feb. 8, when it will begin to share some user information with...
Image: Getty Images Google on Wednesday released version 90.0.4430.85 of the Chrome browser for Windows, Mac, and Linux. The release contains...
Canonical‘s Ubuntu is best known for its Linux desktop, but the company really makes its profits from the cloud and...
Security, in both the physical and digital sense, is imperative for companies to deter trespassers and would-be thieves, as well...
Cyberattacks of all types are an increasingly large problem for all organisations, and as a result many are turning to...
Apple For the past few years, I’ve been wondering how the Intel era was going to end. At Apple’s Unleashed...
From COVID-19 to economic rollercoaster to election mayhem, 2020 is a year we’d all rather forget. But before we start looking...
Open-source software contributes £43.15 billion ($59 billion) each year to the UK’s gross domestic product (GDP) and brought an estimated...