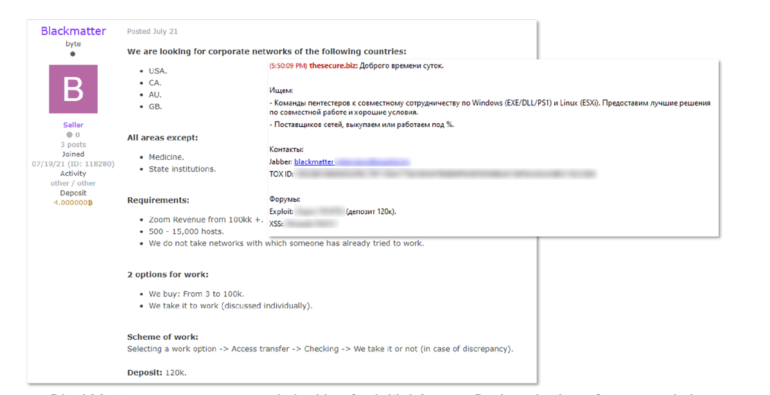
Researchers have explored what the perfect victim looks like to today’s ransomware groups.
On Monday, KELA published a report on listings made by ransomware operators in the underground, including access requests — the way to gain an initial foothold into a target system — revealing that many want to buy a way into US companies with a minimum revenue of over $100 million.
Initial access is now big business. Ransomware groups such as Blackmatter and Lockbit may cut out some of the legwork involved in a cyberattack by purchasing access, including working credentials or the knowledge of a vulnerability in a corporate system.
When you consider a successful ransomware campaign can result in payments worth millions of dollars, this cost becomes inconsequential — and can mean that cybercriminals can free up time to strike more targets.
The cybersecurity company’s findings, based on observations in dark web forums during July 2021, suggest that threat actors are seeking large US firms, but Canadian, Australian, and European targets are also considered.
Russian targets are usually rejected immediately, and others are considered “unwanted” — including those located in developing countries — likely because potential payouts are low.
Roughly half of ransomware operators will, however, reject offers for access into organizations in the healthcare and education sector, no matter the country. In some cases, government entities and non-profits are also off the table.
In addition, there are preferred methods of access. Remote Desktop Protocol (RDP), Virtual Private Network (VPN)-based access prove popular. Specifically, access to products developed by companies including Citrix, Palo Alto Networks, VMWare, Cisco, and Fortinet.
“As for the level of privileges, some attackers stated they prefer domain admin rights, though it does not seem to be critical,” the report states.
KELA also found offerings for e-commerce panels, unsecured databases, and Microsoft Exchange servers — although these may be more appealing for data stealers and criminals attempting to implant spyware and cryptocurrency miners.
“All these types of access are undoubtedly dangerous and can enable threat actors to perform various malicious actions, but they rarely provide access to a corporate network,” the researchers noted.
Roughly 40% of listings were created by players in the Ransomware-as-a-Service (RaaS) space.
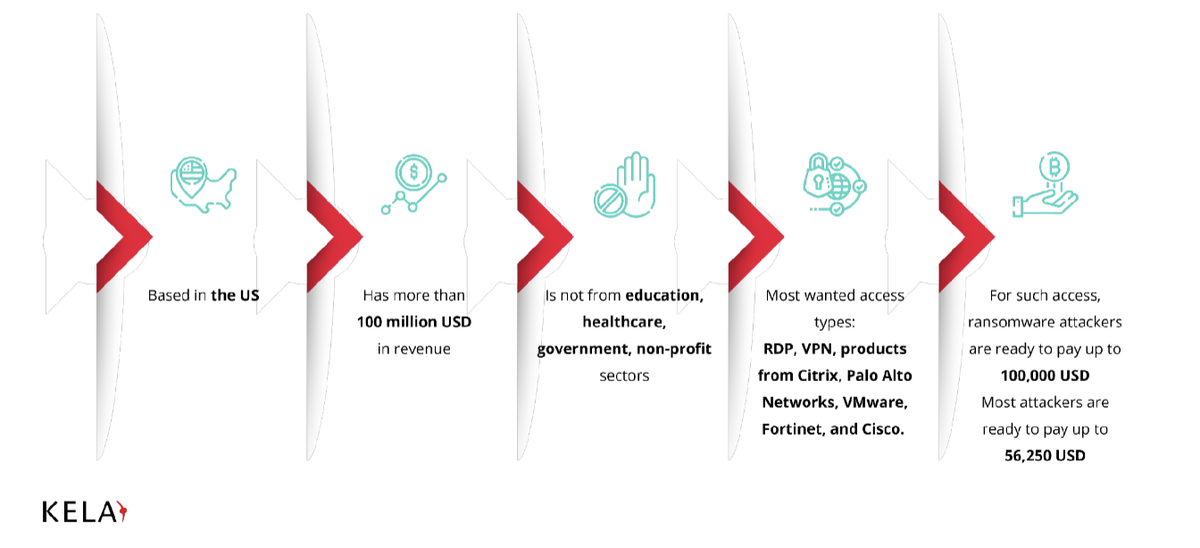

Ransomware operators are willing to pay, on average, up to $100,000 for valuable initial access services.
In a past study, KELA observed another trend of note in the ransomware space: increasing demand for negotiators. RaaS operators are attempting to better monetize the stage of an attack when a victim will contact ransomware operators to negotiate a payment, but as language barriers can cause miscommunication, ransomware groups are trying to secure new team members able to manage conversational English.
Intel 471 has also found that cybercriminals involved in Business Email Compromise (BEC) scams are trying to recruit native English speakers. As phishing email red flags include poor grammar and spelling mistakes, scam artists are trying to avoid being detected at the first hurdle by paying English speakers to write convincing copy.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0