The Research Brief is a short take about interesting academic work.
The big idea
Game theory, which tries to predict how the behavior of competitors influences the choices the other players make, can help researchers find the best ways to share biomedical data while protecting the anonymity of the people contributing the data from hackers.
Modern biomedical research, such as the National COVID Cohort Collaborative and the Personal Genome Project, requires large amounts of data that are specific to individuals. Making detailed datasets publicly available without violating anyone’s privacy is a critical challenge for projects like these.
To do so, many programs that collect and disseminate genomic data obscure personal information in the data that could be exploited to re-identify subjects. Even so, it’s possible that residual data could be used to track down personal information from other sources, which could be correlated with the biomedical data to unearth subjects’ identities. For example, comparing someone’s DNA data with public genealogy databases like Ancestry.com can sometimes yield the person’s last name, which can be used along with demographic data to track down the person’s identity via online public record search engines like PeopleFinders.
Our research group, the Center for Genetic Privacy and Identity in Community Settings, has developed methods to help assess and mitigate privacy risks in biomedical data sharing. Our methods can be used to protect various types of data, such as personal demographics or genome sequences, from attacks on anonymity.
Our most recent work uses a two-player leader-follower game to model the interactions between a data subject and a potentially malicious data user. In this model, the data subject moves first, deciding what data to share. Then the adversary moves next, deciding whether to attack based on the shared data.
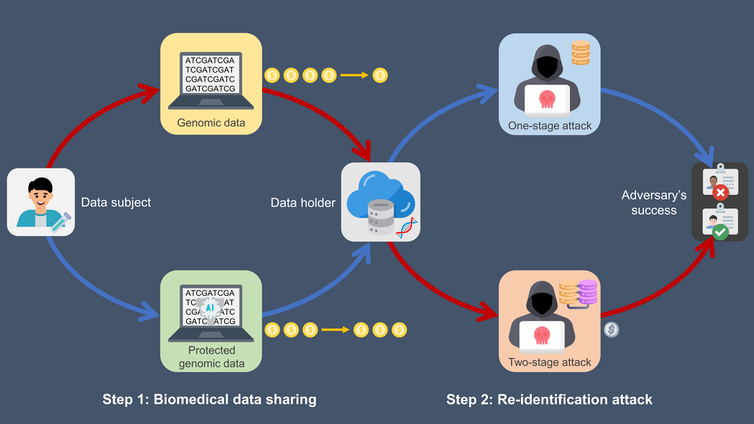
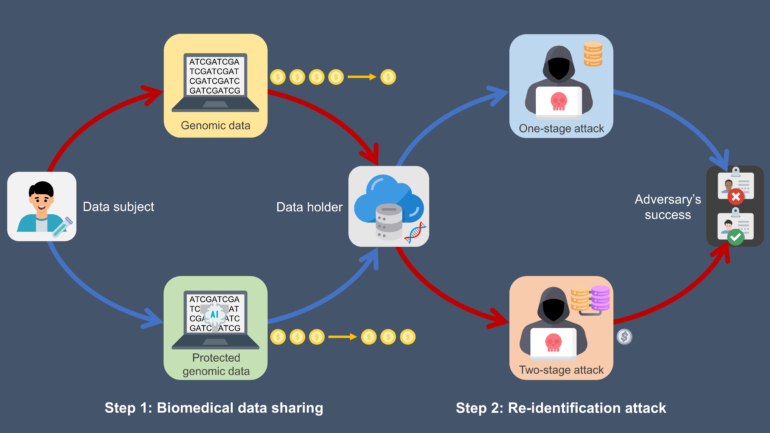
Poorly protected genomic data attacked by someone with access to multiple data sources (red path) is the most at risk, while better-protected genomic data attacked by someone without access to other sources (blue path) is the least at risk.
Vanderbilt University Medical Center, CC BY-ND
Using game theory to assess approaches for sharing data involves scoring each strategy on both privacy and the value of the shared data. Strategies involve trade-offs between leaving out or obscuring parts of the data to protect identities and keeping the data as useful as possible.
The optimal strategy allows the data subject to share the most data with the least risk. Finding the optimal strategy is challenging, however, because genome sequencing data has many dimensions, which makes it impractical to exhaustively search all possible data sharing strategies.
To overcome this problem, we developed search algorithms that focus attention on a small subset of strategies that are the most likely to contain the optimal strategy. We…